Microsoft CA can now issue certificates signed by Quantum-Resistant ECDSA Algorithm: Part 4 - Issuing certificate signed with custom Crypto Provider
Article in the Series
This article is part of a series. The other articles are:
- Microsoft CA can now issue certificates signed by Quantum-Resistant ECDSA Algorithm: Part 1 - Installing ADCS
- Microsoft CA can now issue certificates signed by Quantum-Resistant ECDSA Algorithm: Part 2 - Configure CA to select a custom Crypto Provider
- Microsoft CA can now issue certificates signed by Quantum-Resistant ECDSA Algorithm: Part 3 - Submitting CSR to CA
- Microsoft CA can now issue certificates signed by Quantum-Resistant ECDSA Algorithm: Bonus Part - Are signatures ECDSA compliant?
Introduction
Recall in Part 3, we learnt the steps to submit a CSR as a client on the Windows Server to the CA by using the CA Web Enrollment role.
At this point, a CSR has been submitted to the CA. There is a pending CSR that has yet to be approved by the CA server's administrator.
In Part 4, I will show how to approve the CSR and issue the signed certificate as the CA server's administrator.
Upon approving the CSR, the certificate will be signed through the cryptographic provider that CA has selected to use, which in this series is pQCee Cryptographic Provider. The digital signature on the signed certificate will be quantum resistant as the certificate is signed by ECDSA as the signing algorithm with an additional SPP layer.
Approving the CSR and issuing the certificate signed by SPP algorithm (as a CA server's admin)
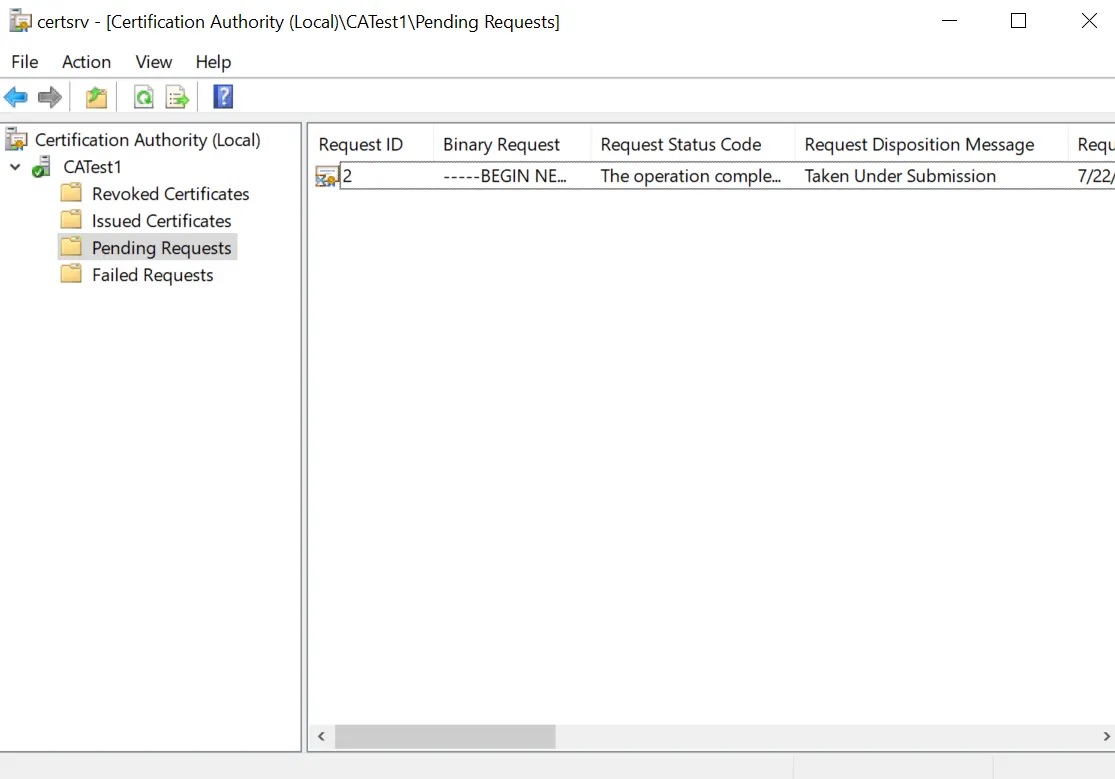
Go to Windows Search Bar, search and open Certificate Authority application. Once opened, go to "Pending Request".
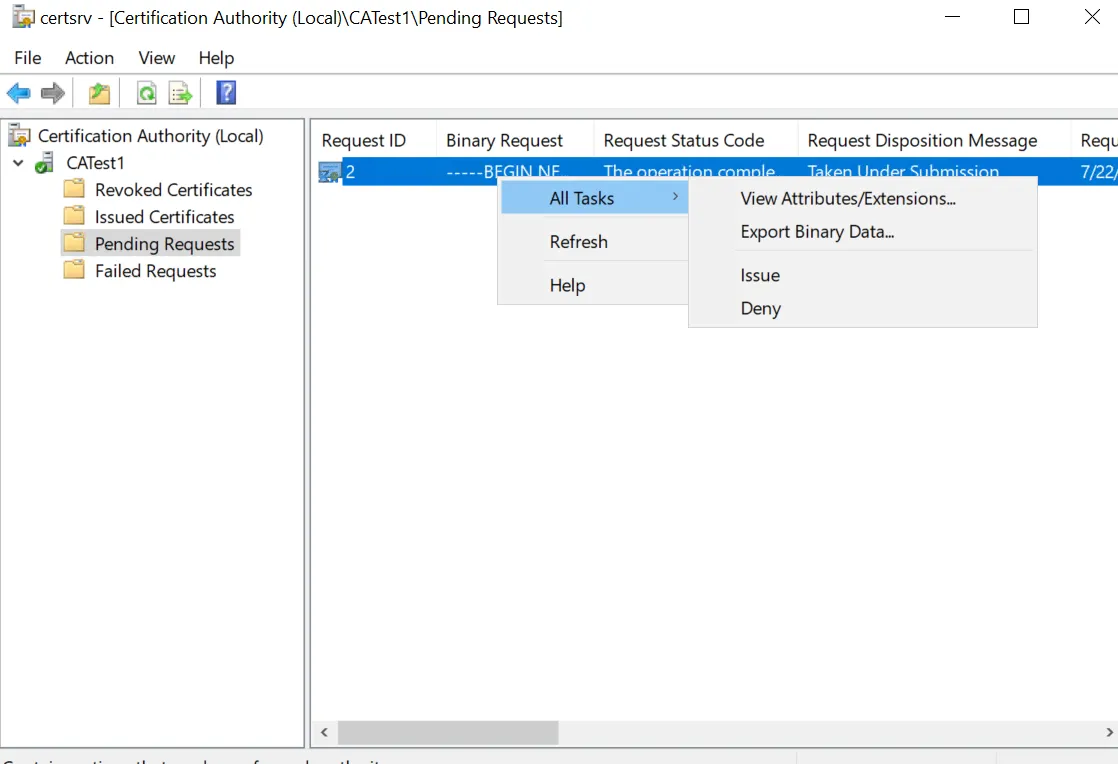
The pending CSRs can be found here. In order to approve the CSR and issue the signed certificate, right click on the CSR and click on "All Tasks". Then, click on "Issue".
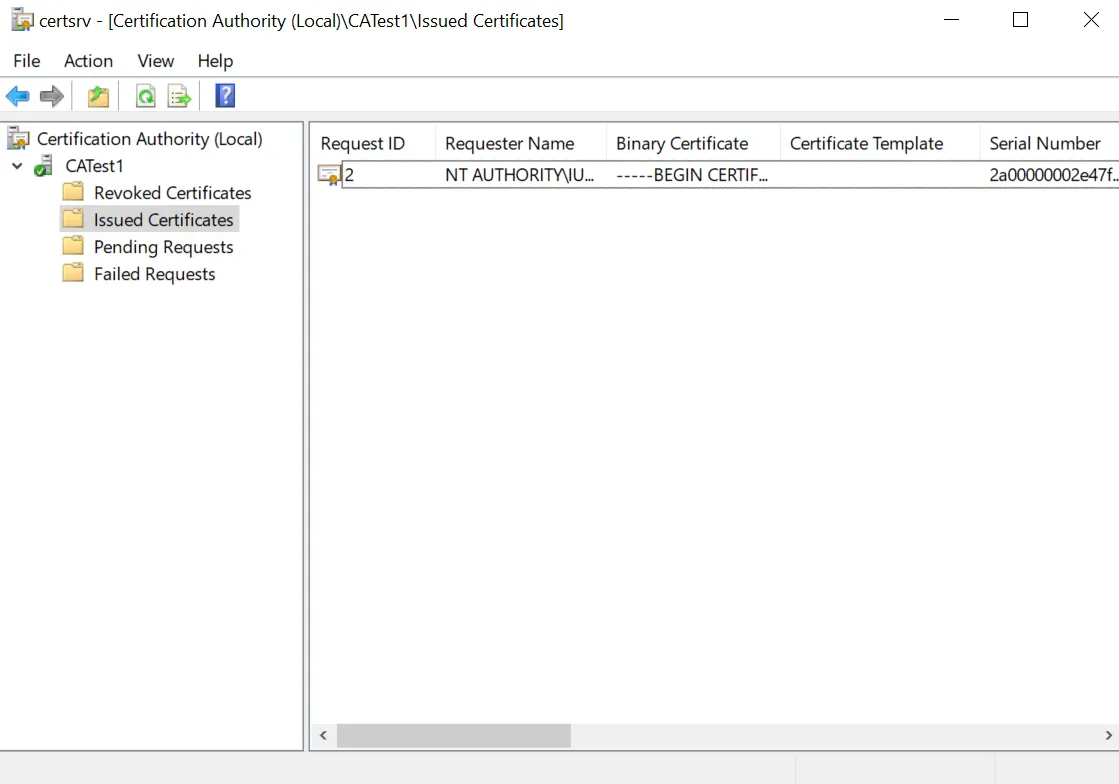
The CSR has been approved and the certificate has been issued. Now, go to "Issued Certificates" and you should see the issued certificate.
The aforementioned certificate, which has been issued by the Standalone Root CA on the Windows Server, has been signed by ECDSA with an additional SPP layer through the pQCee Cryptographic Provider.
Conclusion
Recall that:
- in Part 1, we have learnt the installation steps of ADCS roles (CA and CA Web Enrollment).
- in Part 2, we have learnt the configuration steps of the ADCS roles installed. Most importantly, we have configured CA to select pQCee Cryptographic Provider as the cryptographic provider.
- in Part 3, we have learnt how to submit a CSR as a client on the Windows Server to the CA by using the CA Web Enrollment role to simulate the process of issuing a signed certificate in Part 4.
- in Part 4, we have learnt how to approve the CSR and issue the signed certificate as a CA's server administrator.
By doing the above, this series so far has successfully demonstrated how Microsoft Standalone Root CA can work with a custom cryptographic provider, which provides a signing algorithm to CA's signing operations. In the case of configuring Microsoft Standalone Root CA to select pQCee Cryptographic Provider, I have shown that the signing algorithm provided to CA's signing operations is ECDSA with an additional quantum-resistant SPP layer. As a result, the digital signature on a signed certificate issued by the CA is quantum resistant.
With the additional SPP layer on top of ECDSA, this differs from the conventional signing algorithms (ECDSA, RSA and etc). You may ask "Can the signatures be verified? Are the signatures still ECDSA compliant?"
Stay tuned for a Bonus Part to answer your queries.
Author
Cher Yue Yang
Yue Yang is an intern in pQCee. He marvels at how the cybersecurity landscape is shifting to a post-quantum era in the near future. He is excited to be part of the post-quantum movement before he begins his Computer Science degree.