Introduction
Key management has long been a challenge since the inception
of cryptography. From provisioning to distribution to rotation and expiration, managing
the secrecy of cryptographic keys has plagued modern security systems.
Previously,
the advent of public key cryptography and subsequent development of Public Key
Infrastructure (PKI) enabled scalable key distribution based on asymmetric
encryption algorithms, such as Rivest-Shamir-Adleman (RSA) and Elliptic Curve
Cryptography (ECC). However, the emergence of quantum computers threatens such
classical cryptographic primitives, where algorithms such as Shor’s algorithm can
factor large integers into their primes in polynomial time, rendering RSA and
other encryption schemes vulnerable.
The industry needs to migrate to quantum-safe methods,
and Quantum Key Distribution (QKD) can be used as a part of the defence-in-depth cybersecurity strategy. However, QKD comes
with its own complexities, considering the specialized setup of physical
infrastructure. To work around these limitations, pQCee’s QKDLite offers a
software implementation of a lightweight digital QKD to provide a quantum-safe
solution for current cloud applications.
What is QKD?
Quantum key distribution leverages the properties of quantum
photonics to establish a secret key between two parties
over a quantum channel, typically an optical fiber cable. This differs from classical key distribution methods, which rely on the computational complexity of mathematics for security.
A Quantum Key
Distribution Entity (QKDE) transmits encoded photons to another QKDE for measurement. Due to the no-cloning theorem and the disturbance caused by quantum
measurement, the act of eavesdropping is detectable, so a tamper-evident channel can be established.
The rise of digital QKD
While QKD has significant potential, there are barriers to adoption. One key challenge for the proliferation of QKD networks is the high infrastructure overhead. There are considerable setup costs typically associated with connecting multiple QKDEs over long distances via either optical fiber, laser or satellite links, which are sensitive to environmental noise. Additionally, to receive quantum keys over classical channels, software and cloud applications that integrate with QKDEs must all adopt quantum-safe approaches to maintain end-to-end quantum-safety.
Another limitation is the need for a classically authenticated channel, in addition to the quantum channel, to perform key correctness verification between QKDEs. This creates a dependency on classical security
systems, resulting in the QKD system inheriting the existing cybersecurity risks of a classically authenticated channel.
One possibility to implement QKD today is via a digital QKD approach – a classical-based module that acts like a QKD, yet can
be instantiated much closer to cloud applications. This works around the
current lack of physical infrastructure and integrates with current software systems,
providing a quantum-safe solution usable today.
QKDLite as a digital QKD
QKDLite can function as a digital QKD, providing quantum-safe, ephemeral keys available for use. Keys are generated in one of two ways: by connecting to a pair of QKDEs, or by connecting to a quantum random number generator (QRNG) device or QRNG-as-a-Service.
Paired-QKDE Configuration
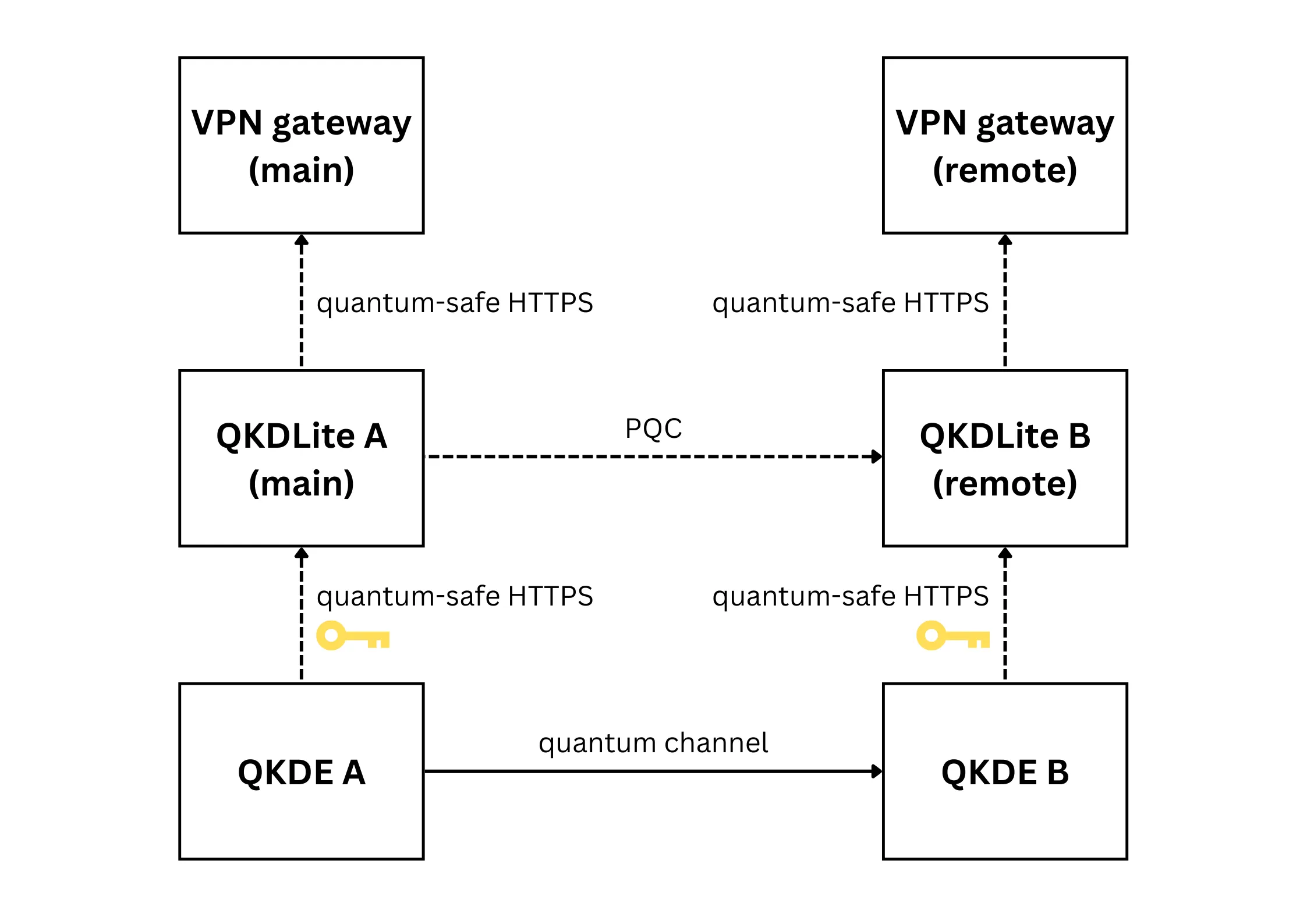
In the case that
two QKDLite instances are connected to a pair of QKDEs over quantum-safe HTTPS,
the main QKDLite instance will request for a quantum key via a REST API (adhering to ETSI protocol) from its connected QKDE. This key is stored by the QKDLite instance (in a HSM, token or local file system). Likewise the remote QKDLite instance will request for the same key from the other QKDE.
In this manner, cloud applications (represented by the VPN gateways in Figure 1) can request for quantum keys from the QKDLite instances.
QRNG Configuration
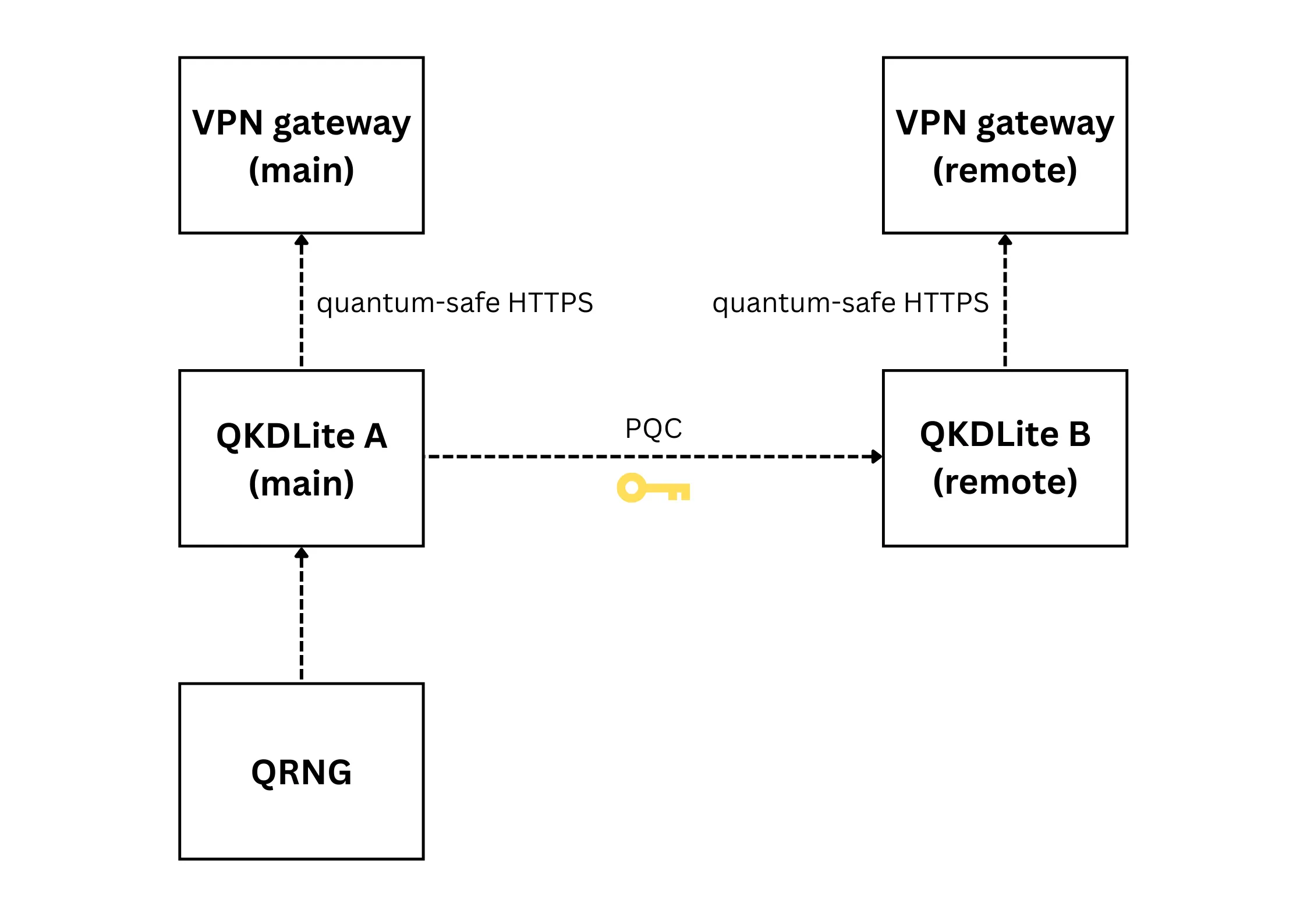
Alternatively,
QKDLite supports internal key creation using quantum random seeds pulled from a connected QRNG device or QRNG-as-a-Service, resulting in quantum keys
that can also be used and stored without a QKD infrastructure. In this
setup, a quantum key is
generated from the QRNG source in the main QKDLite instance and subsequently replicated to the remote QKDLite instance.
In either case,
users have access to a shared set of quantum keys available for
consumption without needing to directly interface with QKDEs. On top of this, QKDLite allows for custom key policy
management: controlling key availability and expiration. The number of keys
always available can be set, as well as how often keys are refreshed,
accommodating for high-volume usage of ephemeral keys that may be needed in
cloud applications.
Use Case: Secure File Transfer
A practical example of using QKDLite is to securely transfer files over the internet. With QKDLite as a digital QKD, the sender and recipient are able to send encrypted files over the internet without having to deal with key management.
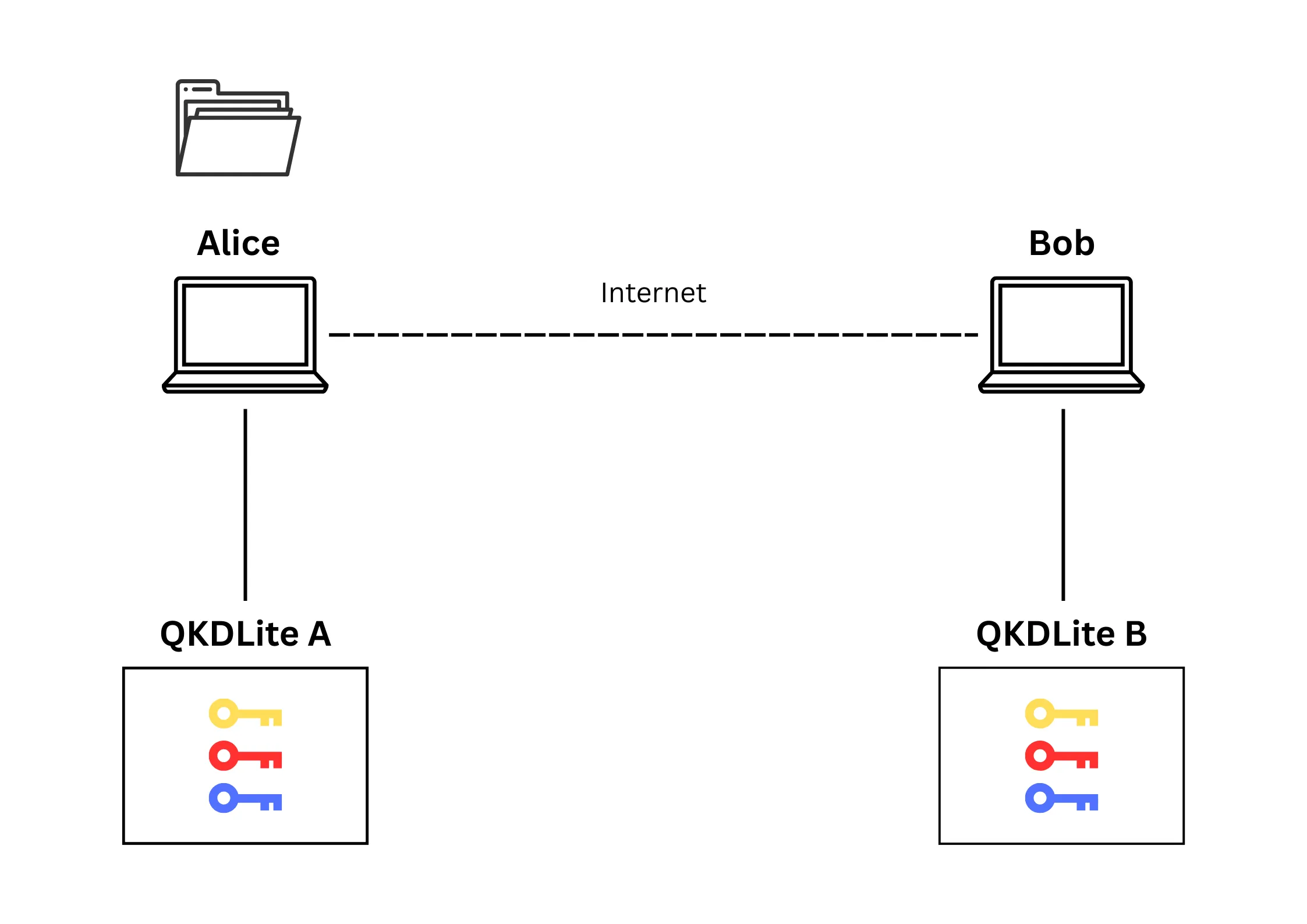
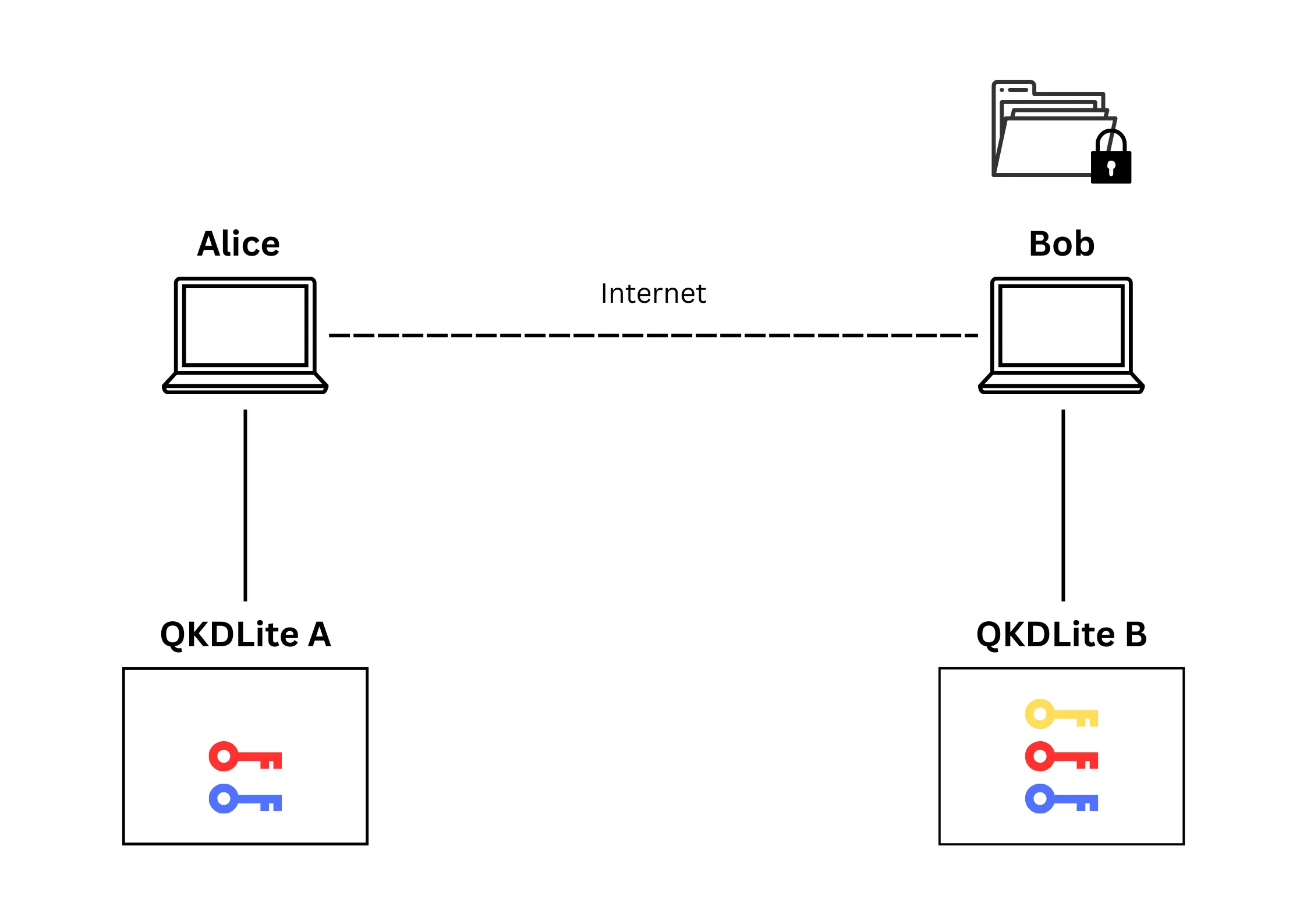
At both QKDLite instances, there are 3 keys set up using the 'paired QKDEs' method. Alice wants to
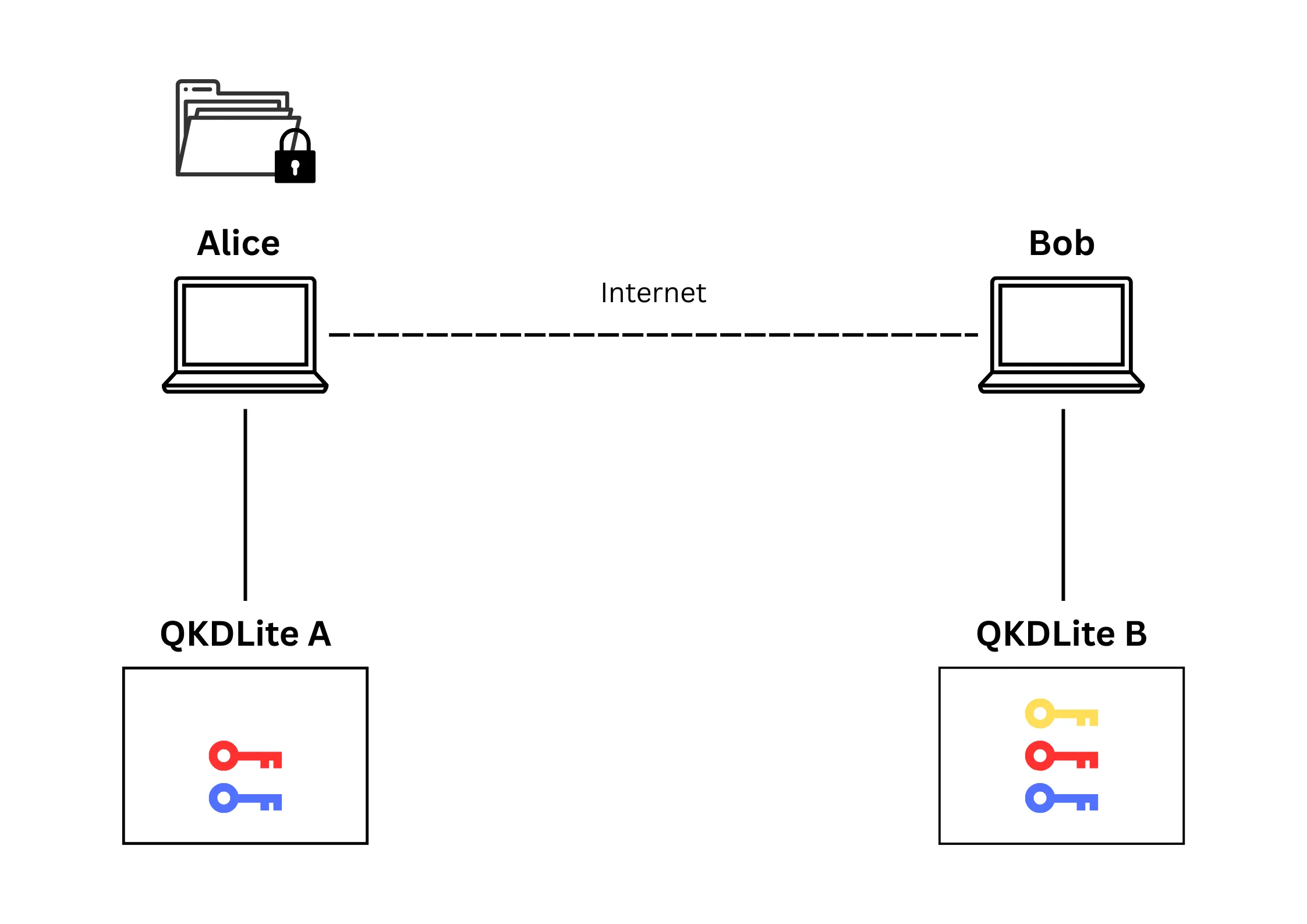
encrypt and send a file to Bob (Figure 3). To encrypt the file, Alice connects to QKDLite A to encrypt the file. This results in the consumption of one key at QKDLite A. A copy of the same key remains at QKDLite B (Figure 4).
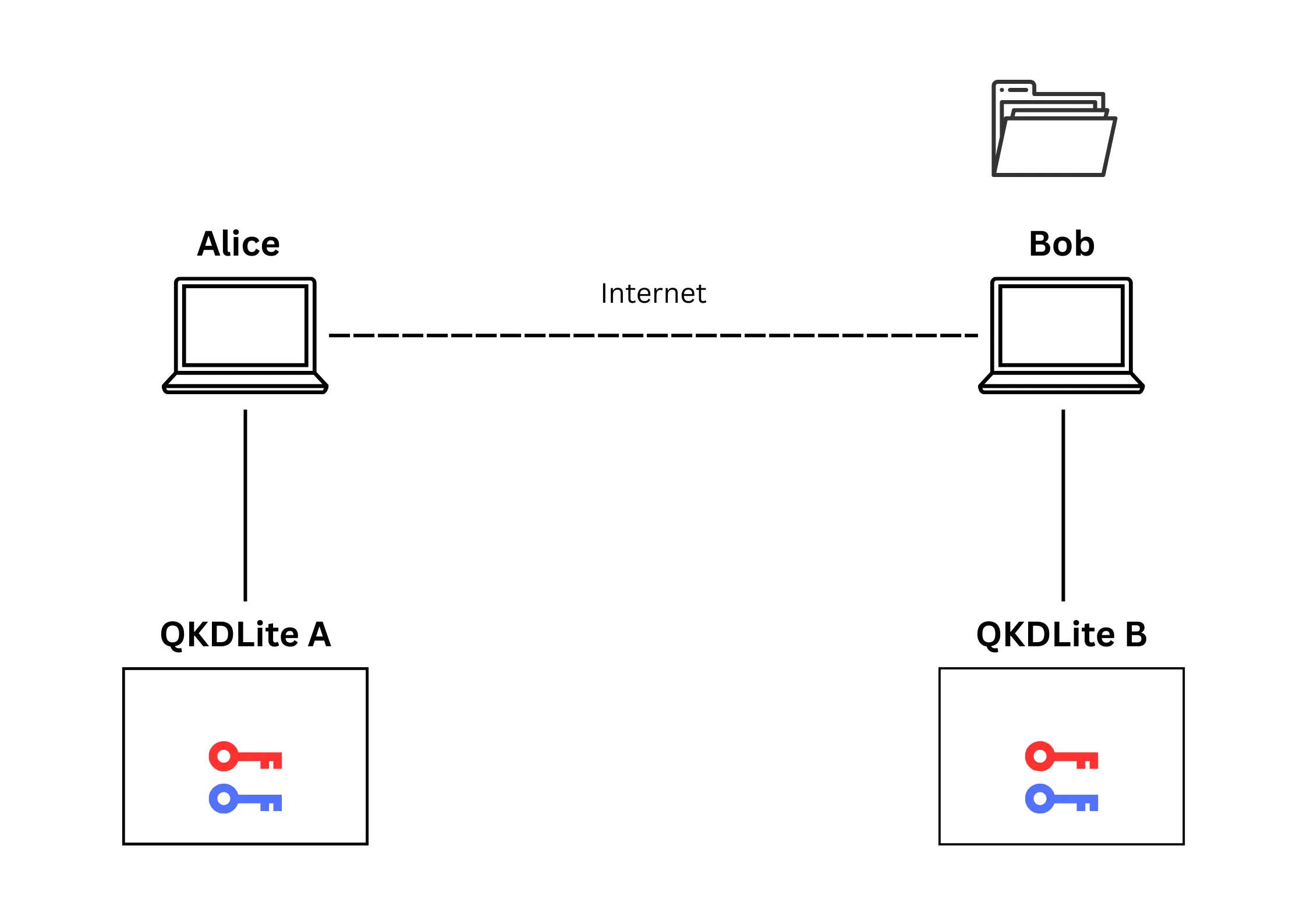
Alice sends the encrypted file to Bob over the internet as an email attachment. Bob receives the encrypted file (Figure 5) and uses the same
key from QKDLite B to decrypt and view the file (Figure 6).
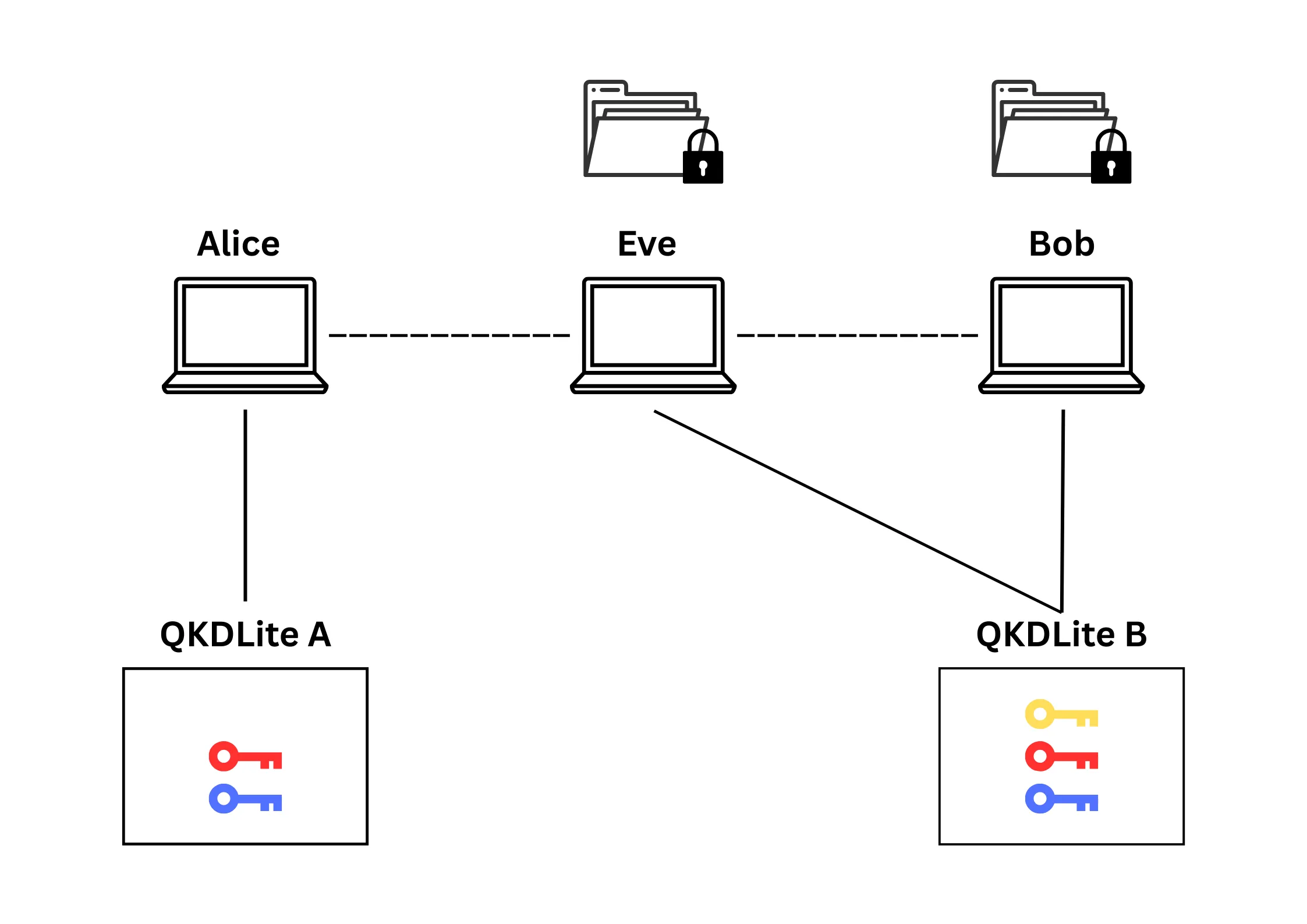
If Eve does not have access to QKDLite B, she does not have access to the decryption key. Even if she intercepts the encrypted file, she will be unable to decrypt and view the file, so the file contents remain safe from Eve.
In the worst case, Eve intercepts the encrypted
file (Figure 7) and has access to QKDLite B. If Eve decrypts the file before Bob, the decryption key (yellow key) will be consumed. Subsequently, when Bob tries to decrypt the file and finds that he cannot, he is notified that the decryption key has been consumed, implying that someone else has already decrypted the file.
This scenario demonstrates tamper-evidence: since only one copy of the same key exists on both QKDLite instances, key consumption can be tracked, enabling the detection of file decryption by unintended parties.
QKDLite for High Availability
By relying on Post Quantum Cryptography (PQC) and QRNG, digital QKDs such as QKDLite can quickly integrate with current software
implementations without massive infrastructure overhead, providing easy access to quantum keys. The advantage is even more apparent for more complex cloud
applications that require high availability and implementation of a fail-safe for
quantum key management. QKDLite can be horizontally scaled such that the
failure of any digital QKD instance does not impact the overall availability of
the key distribution infrastructure.