Introduction
As quantum computing edges closer to practical reality, securing our digital infrastructure against future threats has never been more critical. In this blog post, I’ll walk you through my experience integrating SafeQuard, a quantum-safe encryption/decryption solution by pQCee, into FormSG, an open-source form builder used widely for secure data collection.
This isn’t just a technical deep dive—it's a reflection of why this integration matters. We’ll explore the entire encryption and decryption flow within FormSG, discuss how SafeQuard fits into the existing architecture, how easily it can be implemented into other structures and unpack the challenges and considerations that come with implementing quantum-safe cryptography.
Whether you're a developer looking to future-proof your systems, or just curious about the real-world applications of post-quantum security, this walkthrough offers practical insights into building resilient, quantum-ready web applications.
Quantum Threat and Mitigation by SafeQuard
Quantum Threat: Harvest-Now-Decrypt-Later
The urgency behind quantum-resistant encryption stems from a rapidly emerging cybersecurity risk: Harvest-Now-Decrypt-Later (HNDL). While today’s encryption standards (like RSA and ECC) are secure against classical computers, they’re fundamentally vulnerable to quantum attacks. Once advanced quantum machines arrive, algorithms like Shor’s algorithm will break these encryptions in polynomial time—putting sensitive data at risk.
HNDL is a long-term cyberattack strategy where adversaries steal and store encrypted data today (e.g., via man-in-the-middle attacks or malware) to decrypt it later using quantum computers. This threatens data secured with classical encryption, including:
- Personal Identifiable Information (PII)
- Financial Records
- Government or Healthcare Data
- Corporate intellectual property
Even HTTPS/TLS isn’t foolproof—attackers exploit weak endpoints to harvest data now and wait for quantum decryption.
The attack surface for HNDL lies in communications between users and servers. Examples of exploitation include:
- Interception of data via unsecured networks or compromised CDNs/ISPs.
- Archival of encrypted traffic for future decryption.
- Targeting high-value data (e.g., login credentials, encrypted backups).
At-risk sectors (healthcare, finance, government) must adopt post-quantum cryptography to mitigate this looming threat.
Purpose of SafeQuard and its Functionalities
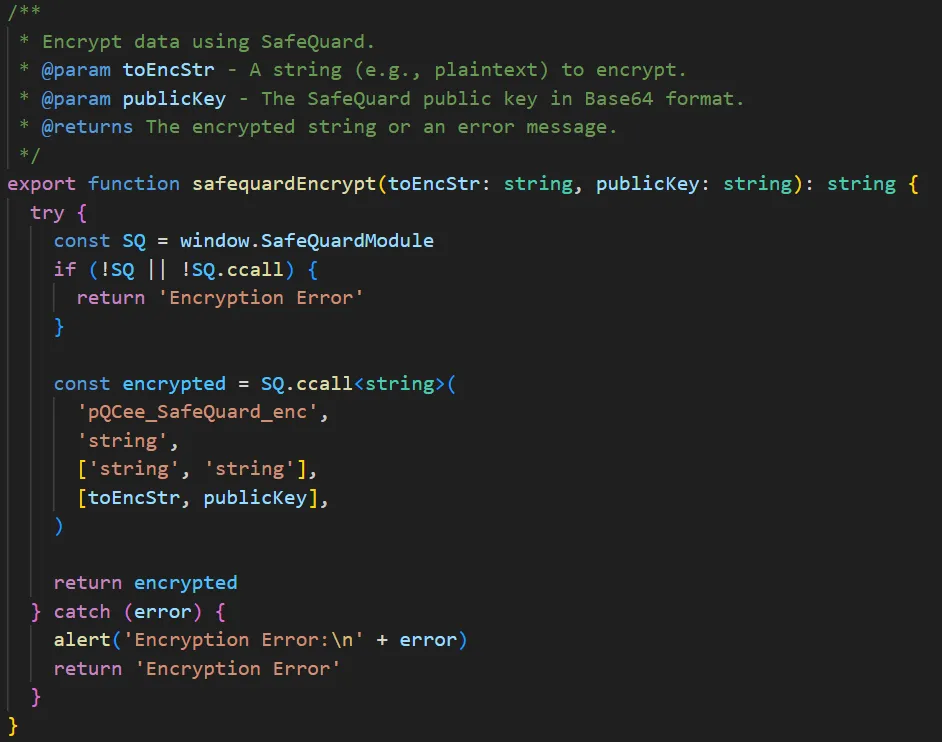
To mitigate this risk, I have integrated SafeQuard by pQCee into FormSG. SafeQuard enables client-side, post-quantum encryption—meaning form data is encrypted inside the user’s browser before it’s transmitted. It uses post-quantum cryptographic algorithms designed to resist attacks from both classical and quantum computers.
- Frontend: Encrypts all form fields, inputs, and attachment metadata via SafeQuard's API
- Backend: Decrypts payloads using SafeQuard's API, making the data usable for downstream processes such as storage or email delivery
- Modular Design: Seamless integration with existing systems
This approach ensures that even if attackers manage to intercept network traffic, the stolen payload remains undecipherable—now and in the future. Ultimately, this isn’t just about protecting data today. It’s about ensuring long-term confidentiality, maintaining public trust, and future-proofing critical systems against a rapidly evolving threat landscape.
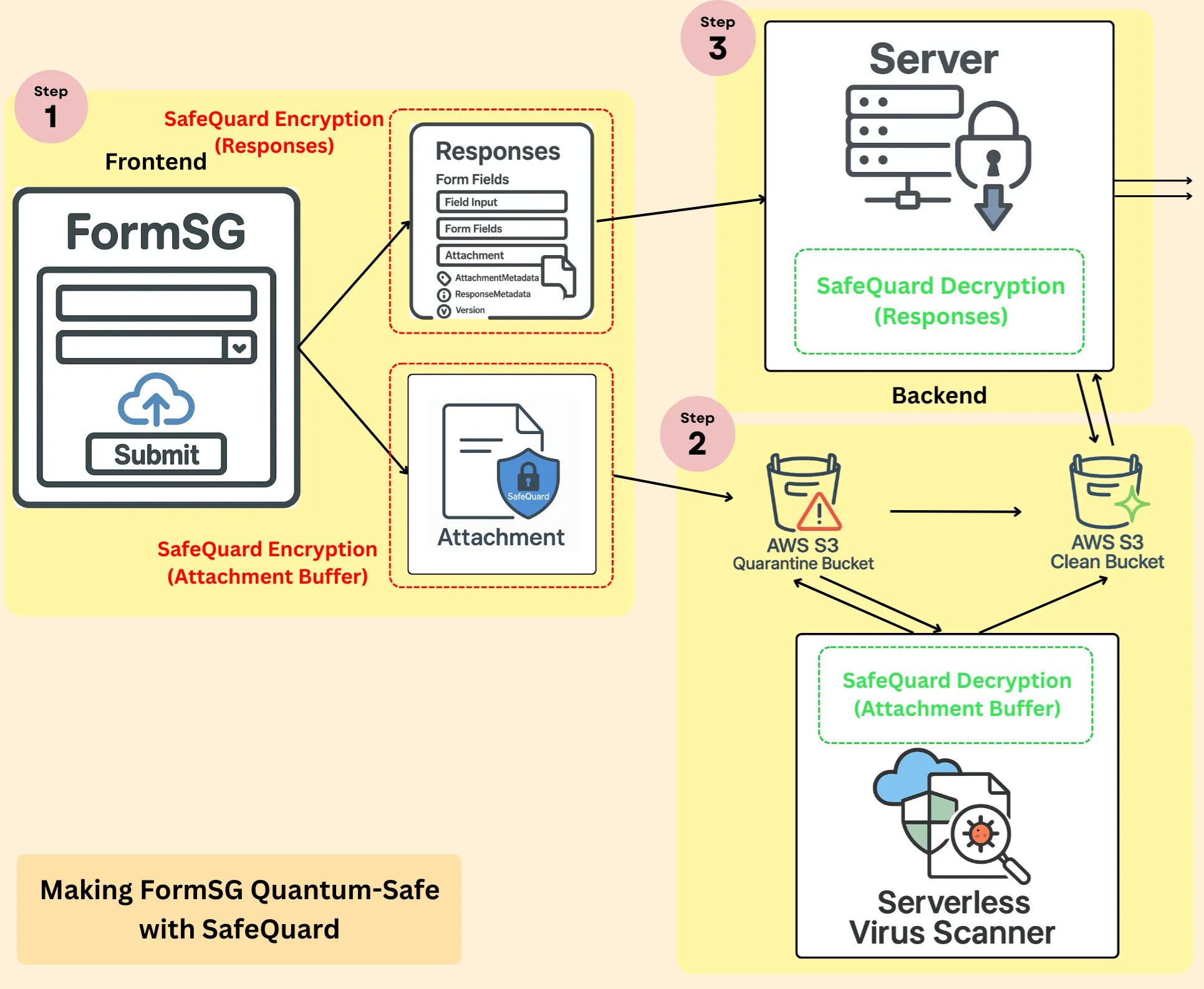
The SafeQuard implementation in FormSG follows three main steps:
- Frontend Encryption – Form data is encrypted using SafeQuard on the client using quantum-safe algorithms before transmission.
- Virus Scanner Decryption – Encrypted files are decrypted for virus scanning to be performed.
- Backend Decryption – Data is securely passed to the backend, decrypted via SafeQuard, and processed.
Refer to the Figure 1 & 2 for a quick overview of how it works.
In the next section, I’ll break down each step in detail—how it was implemented, challenges faced, and key learnings from the process.
Frontend Encryption
The first stage of the SafeQuard integration happens entirely on the client side, where encryption is now built directly into the form submission process.
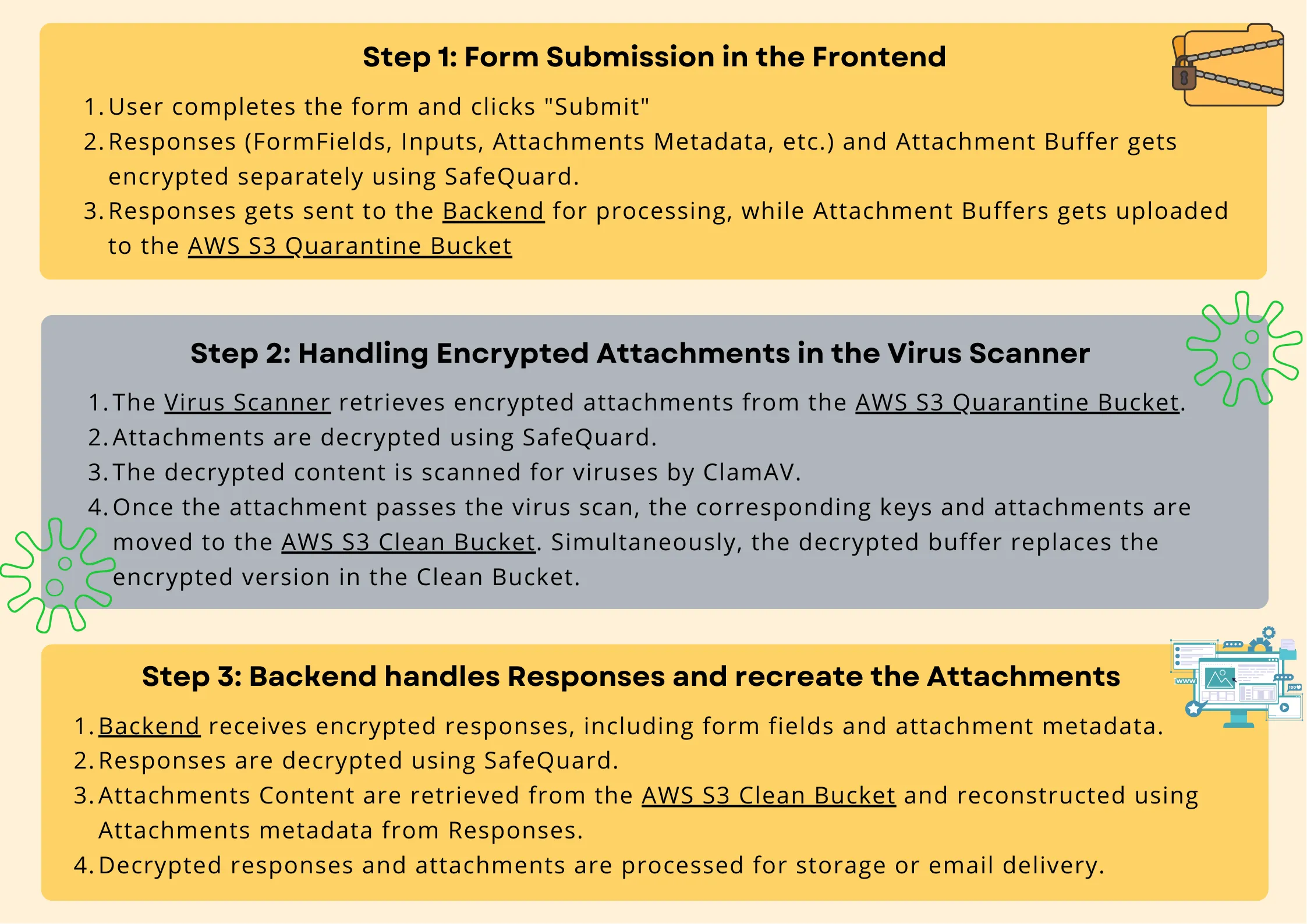
1. Form Creation & Sharing
- Admins can still create and share forms on FormSG as usual—no changes are needed in the form-building workflow.
2. Form Submission & Encryption
- When users fill out and submit a form, two things happen:
- Responses and attachments metadata are immediately encrypted on the frontend using SafeQuard's quantum-safe algorithms and sent directly to the backend.
- Attachments (buffer data) are also encrypted on the frontend using SafeQuard and uploaded to a quarantine S3 bucket in AWS, where they await decryption and scanning before further processing.
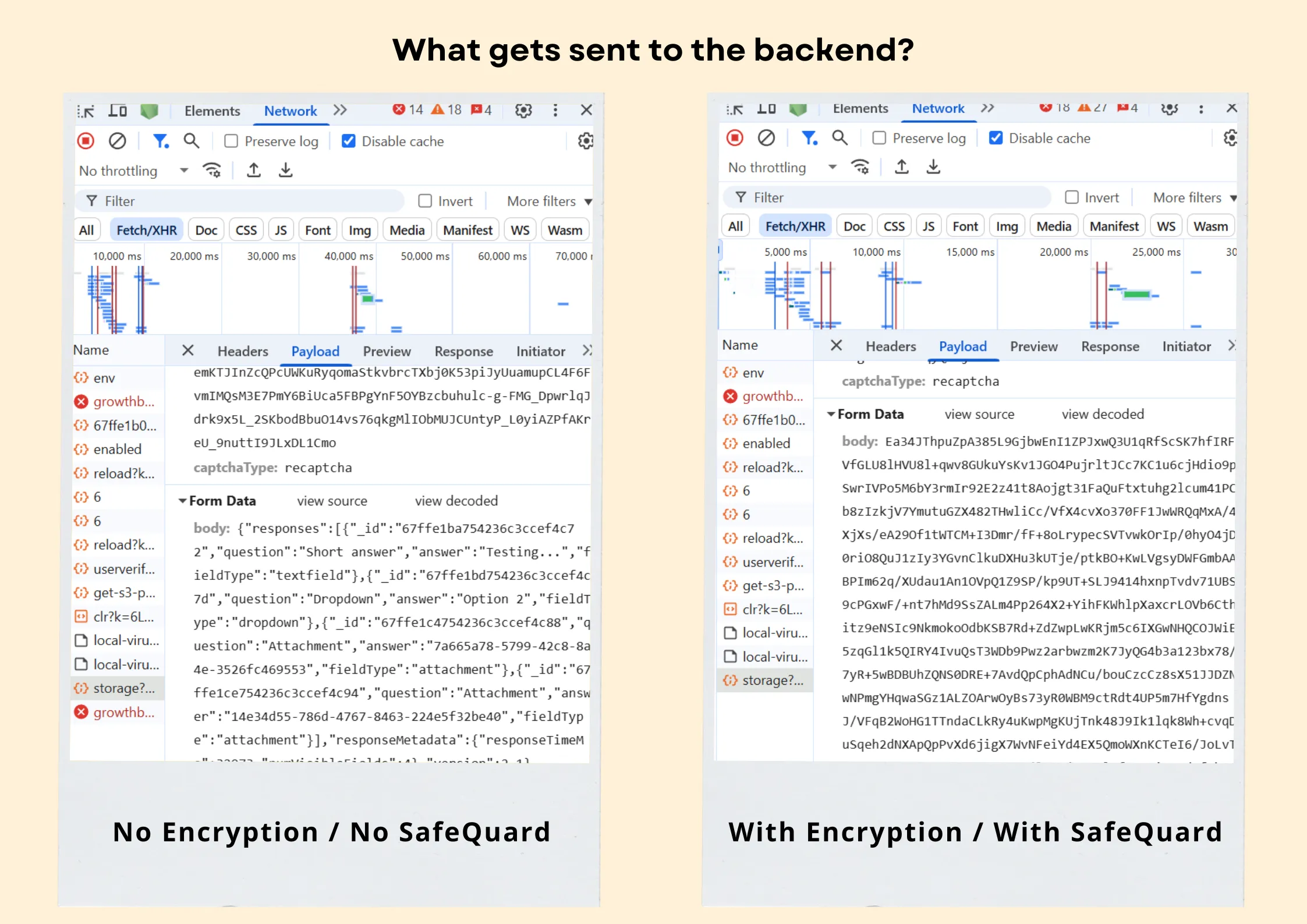
Previous Method: All form data—including responses, metadata, and file buffers—was transmitted over HTTPS but remained unencrypted at the application layer. While TLS provided transport security, the lack of additional encryption meant that if HTTPS were ever compromised, the raw data could be exposed.
Current Solution: Now, every submission is encrypted at the source (client-side) before transmission, using quantum-resistant algorithms. This ensures end-to-end protection, safeguarding data even against future threats like quantum decryption. SafeQuard maintains security beyond just transport-layer HTTPS, providing an extra defense layer where it matters most—before the data even leaves the user’s device..
Virus Scanner Decryption
To maintain the existing security workflow, attachments still need to be scanned for viruses—even after being encrypted on the frontend. This step ensures that functionality remains intact while integrating SafeQuard.
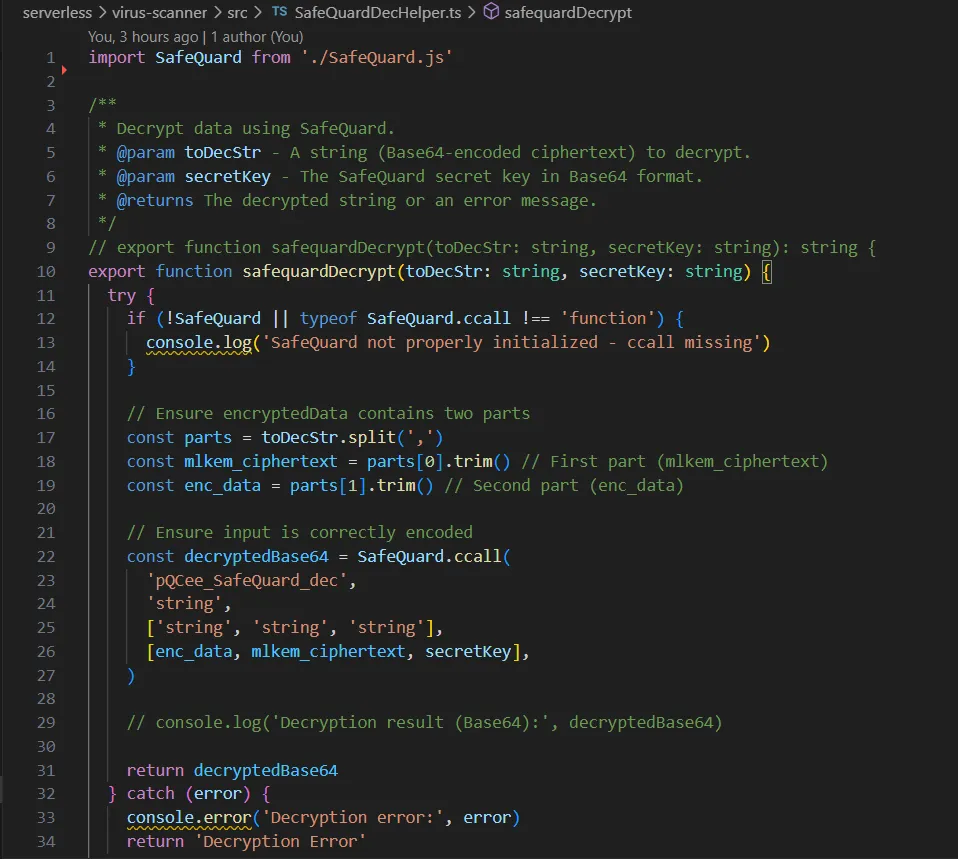
1. Retrieving & Decrypting Attachments
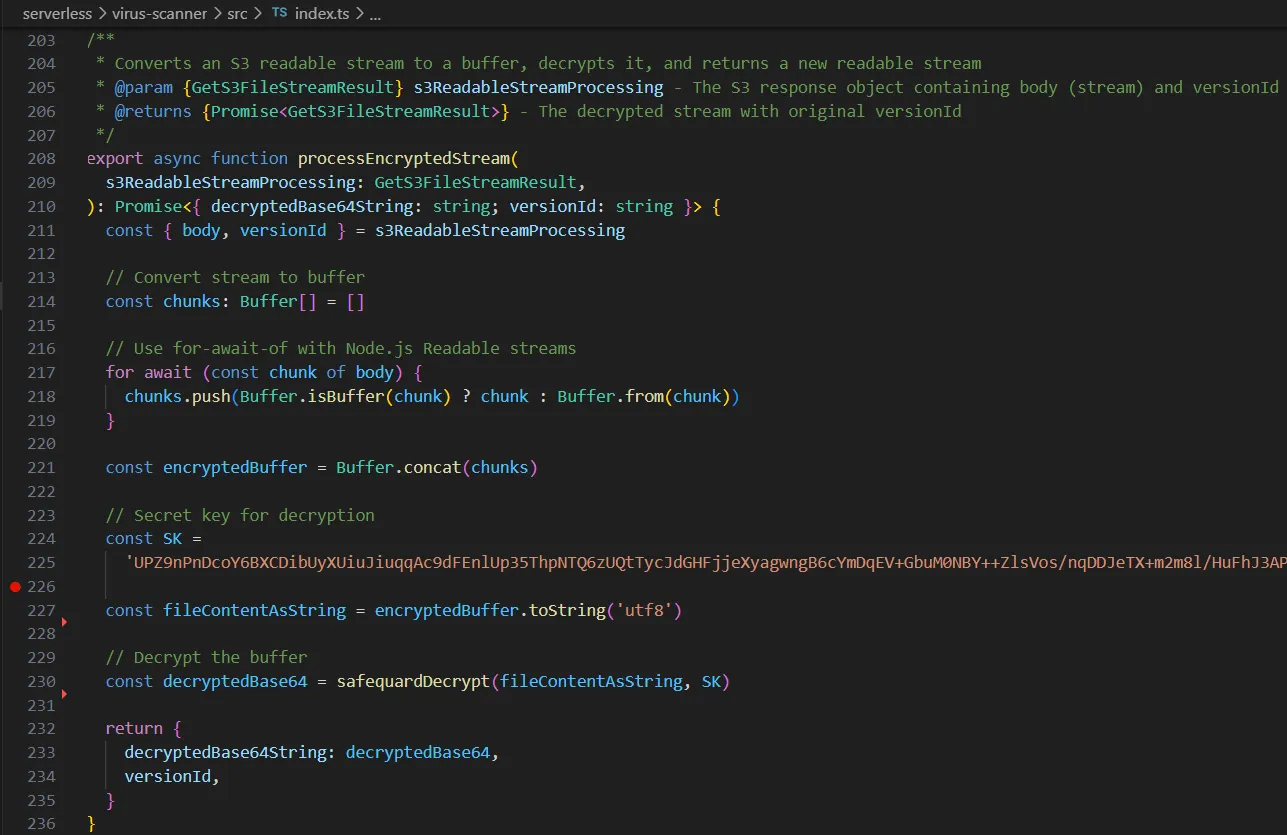
- The encrypted attachment buffer is first retrieved by concatenating the data stream from the AWS S3 Quarantine Bucket.
- SafeQuard decryption algorithms are performed within the virus scanner backend to decrypt the encrypted buffers.
2. Virus Scanning Process
- Once decrypted, the buffer is passed into the virus scanner—just like before the SafeQuard integration.
- After a successful scan, the file data and associated bucket keys are moved from the Quarantine Bucket to the Clean Bucket.
- The decrypted buffer replaces the encrypted one, so the Clean Bucket contains the decrypted version of the attachment.
3. Ready for Backend Use
- With the file safely scanned and stored in the Clean Bucket, it's now ready for secure retrieval and processing by the backend.
Note: This virus scanning and decryption step—detailed above—is actually a sub-step within the larger backend handling phase.
Implementation Note: The example in Figure 7 uses a static secret key for demonstration purposes. In production environments, SafeQuard's API can use Confidential computing (Intel SGX TEE) or HSMs for secure ML-KEM key processing.
Backend Decryption & Data Handling
The final step in the SafeQuard integration ensures that encrypted data—from form responses to file attachments—is properly decrypted and formatted for downstream processing and storage.
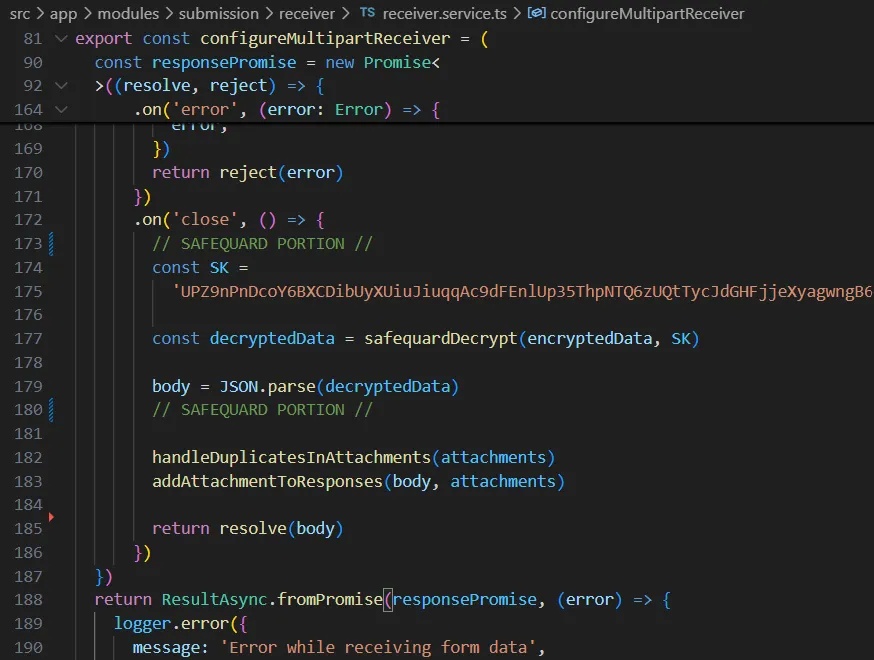
1. Receiving & Decrypting Form Responses
- The backend receives encrypted form responses containing form inputs, fields, and attachment metadata
- Responses pass through middleware layers where SafeQuard decryption is applied
- Data is restored to its original, usable format before continuing through the pipeline
2. Attachment Retrieval
- Middleware handles attachments as previously covered
- After virus scanning and decryption, the backend retrieves cleaned attachment buffers from the Clean Bucket
- Attachment metadata from the response is used to reconstruct each attachment
3. Final Processing
- With all components decrypted and formatted:
- Data is stored in the database
- Information is sent to the mail server
- Maintains the original FormSG workflow functionality
Implementation Note: The example in Figure 8 uses a static secret key for demonstration purposes. In production environments, SafeQuard's API can use Confidential computing (Intel SGX TEE) or HSMs for secure ML-KEM key processing.
Looking back at the integration process, one of the things that stood out to me was how straightforward SafeQuard’s quantum-safe algorithms were to work with. Both the frontend and backend libraries are thoughtfully designed, with clean, well-documented functions that are ready to use out of the box. Most of the heavy lifting was already handled by the SafeQuard files—all I had to do was understand where to plug it into the FormSG codebase.
That said, the key challenge wasn’t so much in using SafeQuard itself, but in understanding how FormSG is structured. FormSG has a well-architected flow, but getting familiar with how data moves across different layers—from the client to the backend, through middleware, and finally into storage—was crucial. Once I had a clear grasp of that, integrating SafeQuard’s encryption and decryption steps felt natural and seamless.
I’ve also implemented SafeQuard in other contexts before—web apps, standalone web pages, and form-based platforms as you can see in FormSG—and the experience has been consistent. Its API design is developer-friendly, and it doesn’t require a deep cryptography background to implement effectively. That’s what makes it powerful: it brings cutting-edge quantum-safe protection to everyday web applications without the complexity you might expect.
Overall, implementing SafeQuard into FormSG was not only technically rewarding but also felt like a meaningful step forward in securing user data against future threats. It’s reassuring to know that such robust security can be added without compromising on usability or developer experience.
Conclusion
As we move closer to a world where quantum computing becomes mainstream, it's critical that we start future-proofing our applications today. Forms—often used to collect sensitive personal or organizational data—are a prime target and must be protected from evolving threats.
Implementing quantum-safe encryption like SafeQuard ensures that data remains secure not just now, but in the years to come. Whether it's forms, web apps, or any data-driven service, adopting these technologies early is a smart and necessary step toward resilient, next-gen security.
| FormSG Without SafeQuard | FormSG With SafeQuard |
| Application Layer (Form Data) | No additional encryption (plaintext) | Post-quantum E2E encryption (data encrypted before sending) |
| Quantum Resistance | Vulnerable to Quantum Attacks | Quantum-Safe |