What is hybrid post-quantum encryption?
Hybrid post-quantum encryption involves combining classical key exchange algorithms with post-quantum schemes to ensure that the eventual data that is encrypted is resistant to quantum attacks. We tell you what and how it is done.
With the new NIST PQC standards freshly announced, we are now seeing a greater interest by organizations to protect data and communications against quantum harvesting attacks.
In a harvesting attack, an adversary can collect the encrypted communications happening between the customers and enterprises today (“harvesting”), and use a quantum computer to decrypt the communications sometime in the near future (“attack”). We expect sensitive data such as authentication credentials (passwords, biometric minutiae, authentication keys), financial transaction details (payee, account numbers, transaction values) and customer information to be targeted by such attacks.
But just implementing the NIST PQC algorithms is not as straight-forward. Current classical algorithms such as RSA and ECC have been tried-and-tested for several decades and we are confident they are secure against everything except quantum. On the other hand, the NIST PQC algorithms have undergone rigorous evaluation over the past 7 years and we are pretty sure they are secure against quantum, but maybe not everything else (e.g. side-channel attacks). So how do we combine the use of classical and NIST PQC algorithms to get the best of both worlds? Enter hybrid post-quantum encryption.
Hybrid post-quantum encryption involves combining classical key exchange algorithms (RSA, ECDH) with post-quantum schemes (Kyber ML-KEM, QKD) to ensure that the eventual data that is encrypted is resistant to quantum attacks. Here are 3 different hybrid approaches that we are seeing in the industry:
- Layered (or double encryption). In the layered approach, an additional NIST PQC layer of encryption is used to encapsulate or wrap-around the the existing classical implementation. The systems that are not exposed to the public continue to operate on classical cryptography while the Internet or public facing communications get an additional protection from quantum attacks. The advantage is that multiple layers of post-quantum cryptography can be applied or removed without affecting the existing application to achieve quantum-safety. The disadvantage is that there will be increased computational and data overheads due to the additional layers. An example of layering is Apple’s quantum-safe messaging PQ3
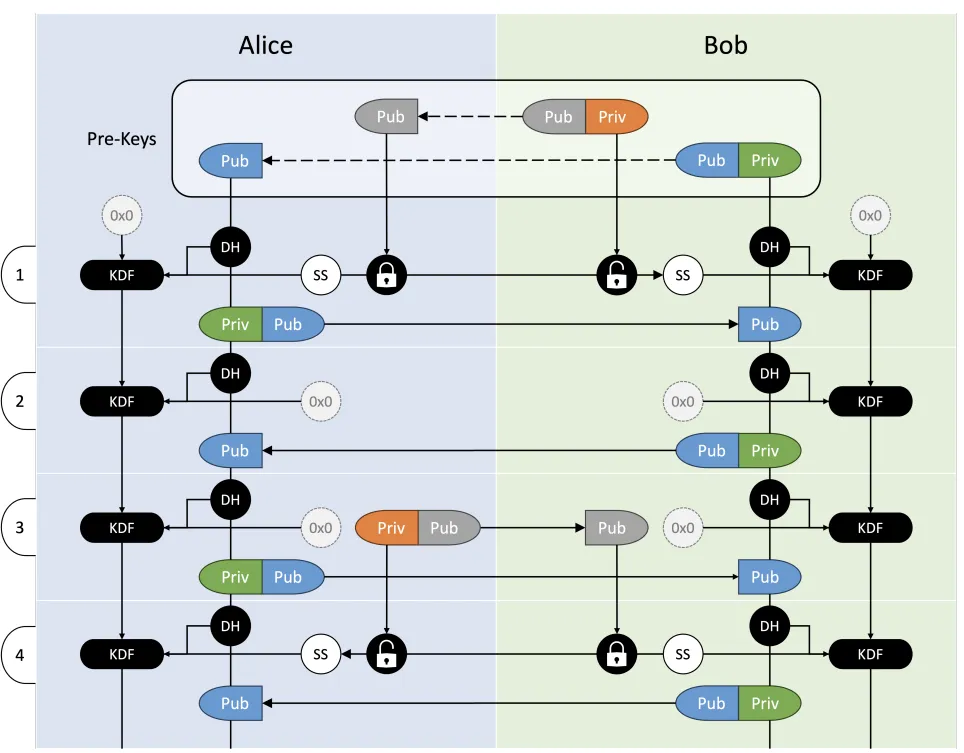
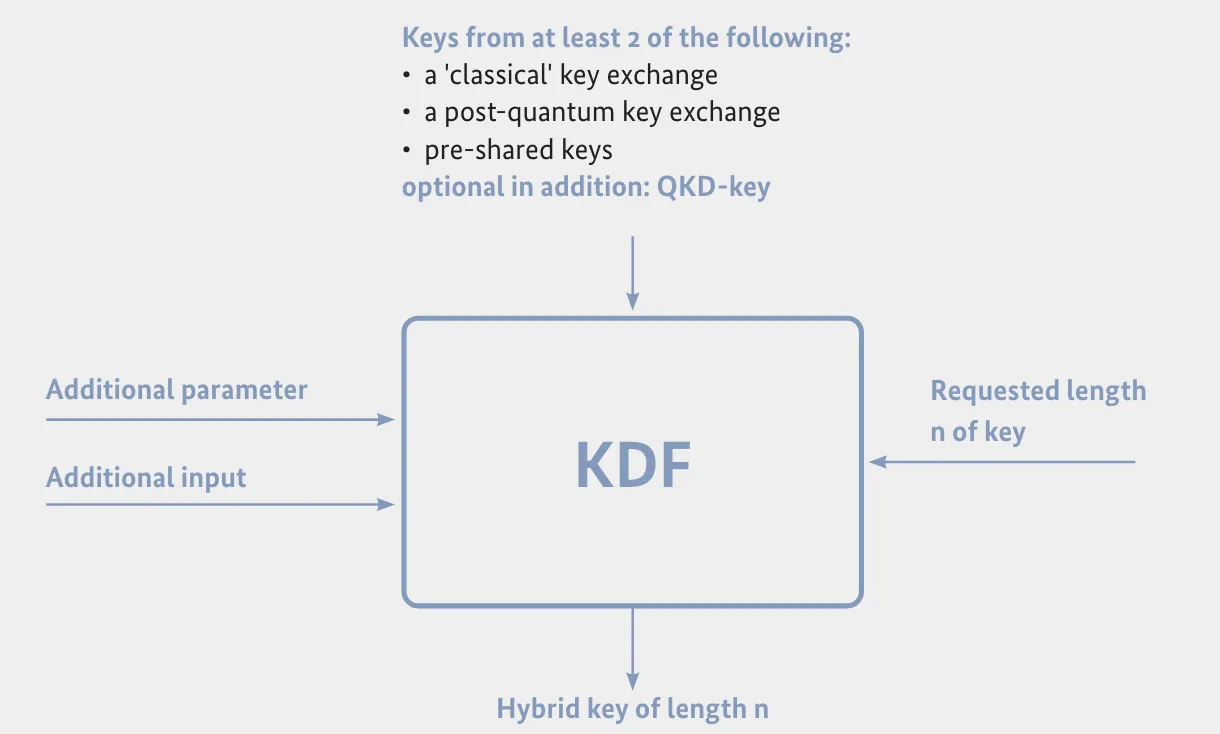
- Composite hybrid. The composite approach focuses on deriving an eventual session encryption key that is quantum-safe. The scheme relies on different key negotiation protocols happening first, e.g. classical ECDH, Kyber ML-KEM and QKD, and then combining all the negotiated keys into a composite key for data encryption. The advantage is that such implementations require the attacker to break all the key negotiation schemes before any compromise happens. The disadvantage is the complexity of the implementation which requires careful design of the protocol and the difficulty of a roll-back. An example of a composite hybrid implementation is BSI’s article on Quantum-Safe Cryptography
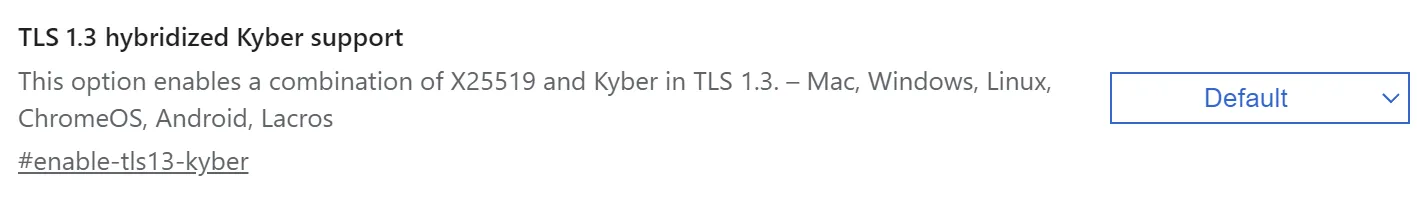
- Interoperable Hybrid. For interoperability and system compatibility, some implementations choose to implement NIST PQC in parallel to classical cryptography. The choice to use either classical and/or NIST PQC happens during the actual use of the application. The goal is to ease the transition into post-quantum cryptography without a big-bang migration approach. The disadvantages are that not all communications are guaranteed to be quantum-safe (since a classical-only option still exists) and a second migration needs to take place to remove out the classical option. An example of such an implementation is Google’s post-quantum support in the Chrome browser
So what is the best approach? We provide a table comparing the schemes below:
| Hybrid Scheme | Layered | Composite | Interoperable |
|---|---|---|---|
| Advantage | Existing application is unchanged, making rollbacks easier | Most secure if implemented correctly | Partial rollouts are possible where some users are using PQC algorithms while others remain on the classical algorithms |
| Disadvantage | Additional overheads on data and processing. | Complex in the design and implementation. Difficult to rollback. Least crypto-agile. | Not all communication is quantum-safe. Requires a second migration to remove the classical option |
| Focus | Balance between security, ease of implementation and rollback | Security. All key negotiation algorithms need to be broken at compromise | Pilots can be carried out in real-life deployments without affecting most users. |
| Crypto-agility | At implementation | At design | At use |
| Recommendation | Best for standalone applications whose data exposure is well understood | Best for industry-wide protocols which are require multiple parties to participate in the design and implementation | Best for experimentation where many of the factors are still unknown or not within your control |
So there you have it. The next time you hear about hybrid post-quantum encryption, find out what is the underlying scheme and decide if it is appropriate for you. Post-quantum security is here to stay and can already be implemented. Stay tuned for the next topic on hybrid post-quantum digital signing.
Author
Tan Teik Guan
Teik Guan is CEO of pQCee.com. He works in the niche area of cryptographic security design and integration, having implemented numerous successful projects for banks, government agencies and enterprises. He holds a BSc and MSc from NUS and a PhD from SUTD.