Sneak preview: NIST PQC certificates on Microsoft Windows
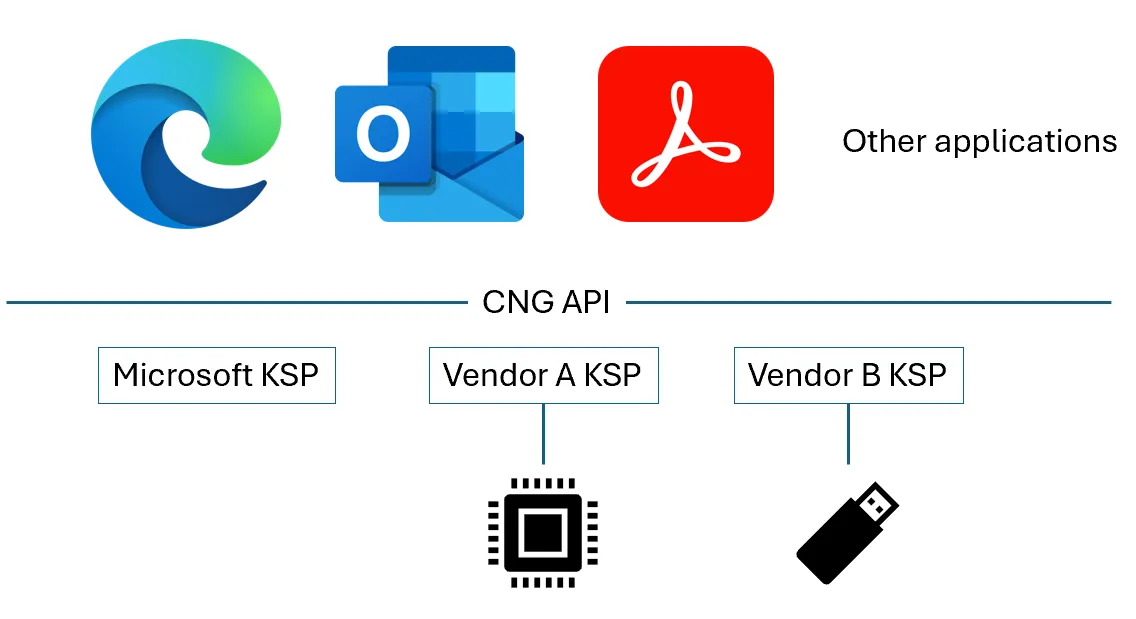
A core part of how applications on Microsoft Windows make use of cryptographic services on the platform is via the Cryptography API: Next Generation (CNG).
Above the CNG API, applications only need to call the necessary cryptographic APIs to create / encrypt / decrypt / sign / verify / derive / import / export / delete the keys and certificates without needing to worry about how the secret material is protected or how the cryptographic operations are carried out.
Below the CNG API, cryptographic vendors provide Key Storage Providers (KSP) which do the heavy lifting of actually performing the key operations (be it in Hardware Security Modules, Smartcards, USB dongles, software, etc), and return the results of execution to the calling application.
And the CNG layer works to abstract the complexity of the cryptographic implementations, while providing interoperability (and agility) across different vendors.
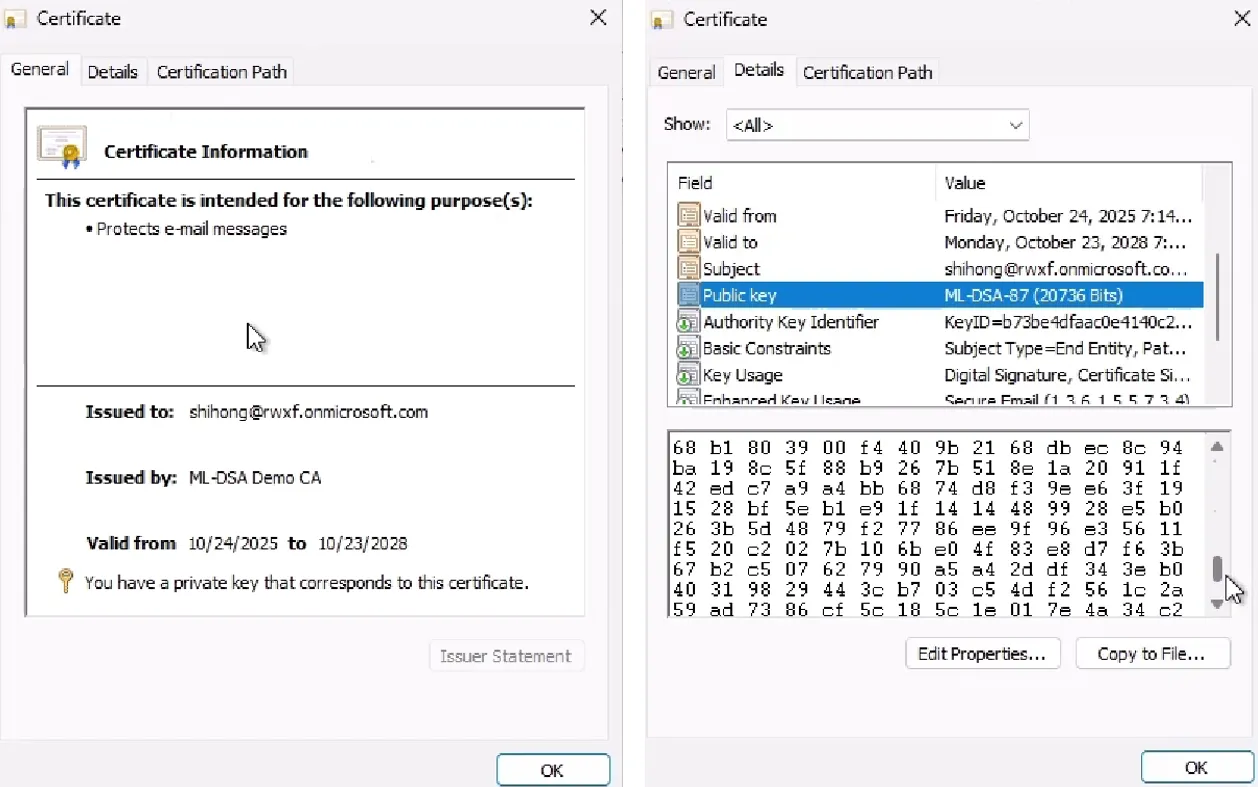
With the threat of quantum looming, all these KSPs will need to be upgraded or replaced with those capable of carrying out post-quantum cryptography. Here's a preview of pQCee's Cryptographic Provider running in Windows Insider that is able to support the NIST PQC (ML-DSA and SLH-DSA) algorithms.
The following video will show the following steps:
- We first use OpenSSL v3.5 to generate and verify the ML-DSA and SLH-DSA certificates.
- We then register the pQCee Cryptographic Provider into the Windows machine
- Next, we import both the ML-DSA and SLH-DSA certificates into the Microsoft certificate store.
- Finally, we use the certutil utility in Windows to run and verify both the ML-DSA and SLH-DSA keys and certificates.
Want to know more? Please contact info@pqcee.com