Post‑Quantum Security Levels Explained: How Secure Is the Internet in 2026?
Why “Quantum‑Safe” Is Not a Yes or No
“Quantum‑safe” is often treated as a yes‑or‑no label — a system is either quantum‑safe or it is not. In practice, post‑quantum security comes in several clearly defined levels, each with different implications for risk, performance, and how long data remains protected. Understanding these levels is important for systems that must remain secure into the 2030s and beyond.
To address this, the U.S. National Institute of Standards and Technology (NIST) defined five post‑quantum security categories as part of its standardization work. These categories provide a common way to compare technologies and to decide how much quantum resistance a system actually requires.
Post-Quantum Security Levels - Simplified
| Baseline Security Strength | NIST Category(s) | Session Key Establishment Method | Data Encryption Algorithm | Digital Signing Algorithm |
|---|---|---|---|---|
| 128 bits | Levels 1 - 2 | ML-KEM-512 | AES-128 | ML-DSA-44, SLH-DSA-*-128s/f |
| 192 bits | Levels 3 - 4 | ML-KEM-768, X25519MLKEM768 | AES-192 | ML-DSA-65, SLH-DSA-*-192s/f |
| 256 bits | Level 5 | ML-KEM-1024 | AES-256 | ML-DSA-87, SLH-DSA-*-256s/f |
The five NIST-defined quantum-safe security levels, however, are based on two underlying types of computational hardness. Levels 1, 3, and 5 defines security as difficulty to brute-force the AES symmetric cipher; Levels 2 and 4 defines security as difficulty to perform collision attacks against the SHA-2/3 hash family.
In practice, they can be grouped into three baseline security strengths, summarised in the table above. Each row in the table represents a baseline level of protection against both best-known classical and quantum attacks. Some familiar session key establishment methods (such as RSA, DH and ECDH) are excluded from the table above, because they are susceptible to quantum attacks.
What “Quantum‑Safe” Means for the Internet in 2026
As of late 2025, internet giants are reported to have migrated 50% of human-intiated traffic to hybrid post-quantum encryption (e.g., X25519MLKEM768 is a combination of a classical algorithm with a post‑quantum algorithm used in the same TLS 1.3 handshake) to provide resistance against the "harvest now, decrypt later" ("HN,DL") quantum threat.
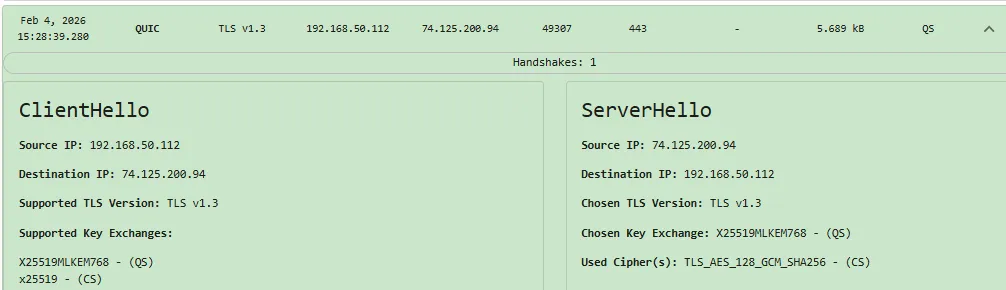
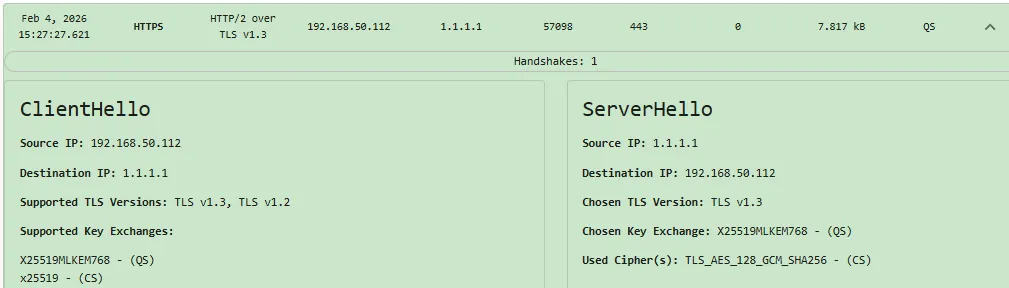
At first glance, migrating human-initiated traffic to the session key establishment method X25519MLKEM768 seems to provide a 192-bit baseline security strength against the "HN,DL" quantum threat. Using packetQC to audit the TLS handshake parameters (see Figures 1 and 2 above), the preferred data encryption algorithm selected by major internet systems seems to be AES-128.
By the weakest link security principle, the baseline security strength achieved is reduced to 128-bit baseline security strength. CNSA 2.0 requires migration to 256-bit baseline security strength against the "HN,DL" quantum threat.
Although not shown in this article, the digital signature algorithm used in the certificates for major internet systems are using either RSA or ECDSA, which are both susceptible to the "trust now, forge later" ("TN,FL") quantum threat. "TN,FL" is the threat where a quantum computer enables attackers in the future to forge digital signatures and certificates that are actively in use and trusted now.
Where We Actually Stand
By 2026, the question is no longer whether post‑quantum security is needed, but how fast organizations can inventory, prioritize, and migrate systems that were never designed for cryptographic agility. NIST now explicitly recommends that organizations begin deploying standardized post‑quantum algorithms and planning the retirement of quantum‑vulnerable schemes well before 2035.
Have you begun your migration to a post-quantum future?
Author
Nicholas Ho
Nicholas seriously enjoys learning new knowledge. He is so serious about it that his hobby is to collect hobbies. His most enduring hobby, since 1997, is to continuously explore the ever-evolving domains of applied cryptography, software development, and cybersecurity. His latest aspiration is to add the word quantum in front of each of these 3 domains. Nicholas is currently a Senior Cryptographic Engineer at pQCee.com. Akin to many Singaporeans, he also enjoys collecting popular certifications, including a CS degree, an Infocomm Security masters, CISSP, and CISA.