How to make strongSwan Quantum-safe
Introduction
StrongSwan, an opensource IPSEC VPN, relies on IKEv2 with Diffie-Hellman, a widely used method for key exchange, which is vulnerable to Harvest Now, Decrypt Later (HNDL) attacks. In HNDL attacks, encrypted traffic is collected today and retrieved subsequently to be decrypted in the future when quantum computers can break the classical encryption, exposing all previously secured communications.
To combat this, strongSwan supports RFC 8784 which defines the use of Post-quantum Pre-shared Keys (PPKs) to add an extra layer of quantum security into the mix. However, the standard strongSwan implementation relies on PPKs which are manually (and often statically) configured in configuration files, which is not ideal. Good security practice requires PPKs to be dynamic (i.e. changing with each session) and should not be cryptographically related to each other for forward secrecy.
Solution
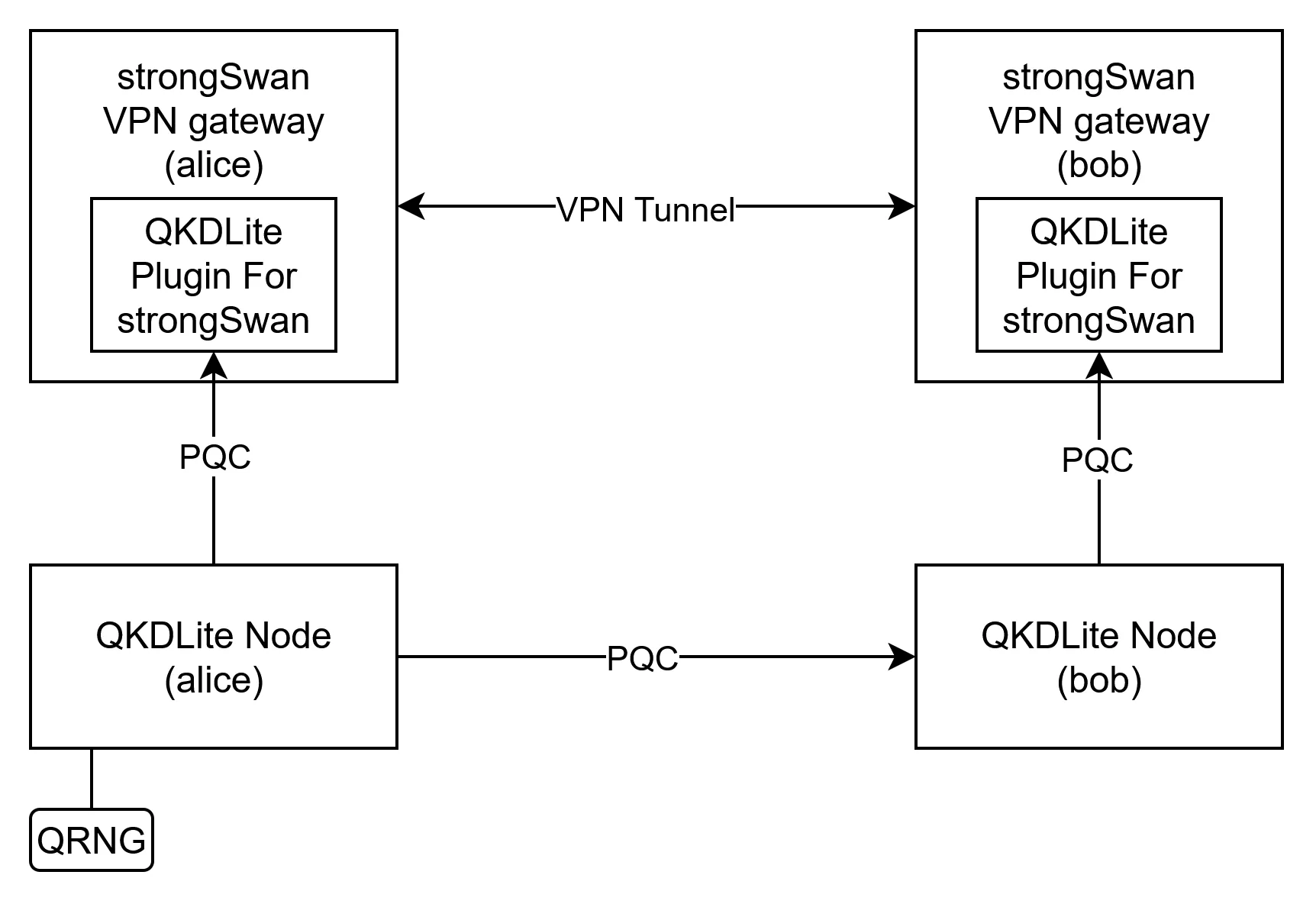
This is where the QKDLite Plugin for strongSwan comes in. It is a software plugin which connects strongSwan to any QKD device supporting ETSI GS QKD 014 API. Once connected, strongSwan can then retrieve quantum-generated random keys from the QKD devices, and use these random keys as dynamic PPKs.
In our implementation shown below, we use the QKDLite plugin for strongSwan to retrieve PPKs from QKDLite, a quantum key management system by pQCee that is compliant with the NIST PQC standards. The plugin integrates directly with strongSwan's credential management system, replacing static configurations with real-time key retrieval via QKDLite.
Each time a strongSwan VPN starts a new connection, the plugin will open a quantum-safe mutual TLS ETSI QKD 014 connection to its respective QKDLite node to retrieve a new PPK. Each PPK is identified with a unique Key ID, and will be removed from the QKDLite node once it is retrieved ensuring that PPKs are never repeated. The source of randomness of the PPKs are enhanced with the use of a Quantum Random Number Generator (QRNG) as an input.
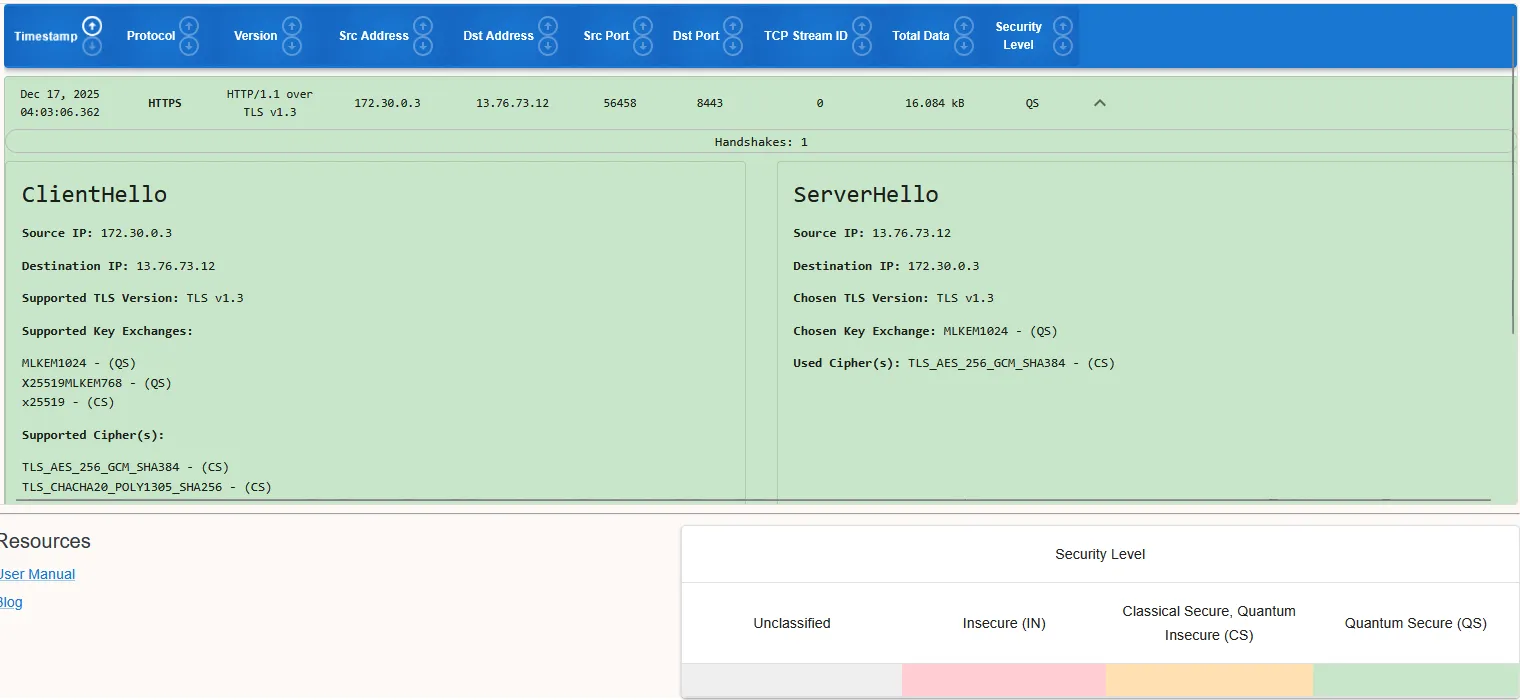
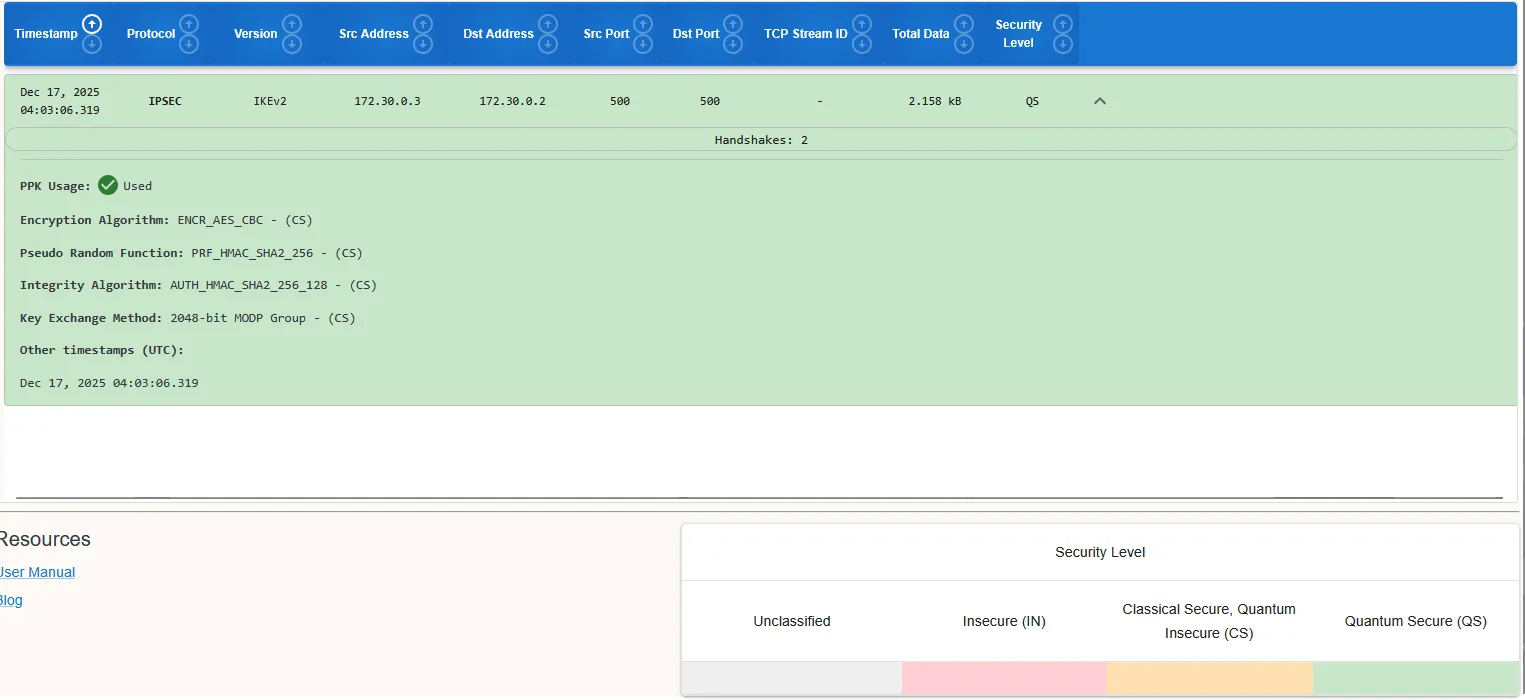
Below images showcases the connections being quantum-safe between the plugin, QKDLite node and the strongSwan VPNs, analyzed with PacketQC.
The QKDLite plugin for strongSwan is designed for hassle-free deployment—no need to rebuild strongSwan from source or change the strongSwan source code.
The plugin is built on top of strongSwan's native libraries to achieve seamless compatibility with existing strongSwan installations. The specific versions we tested on are:
- Ubuntu 22.04
- strongSwan 6.0.3
Conclusion
With the impending threat of quantum computers, the need for quantum-safe communication is crucial. By enabling the quantum-safe solution for strongSwan, we expect that many of the thousands of strongSwan users in the community can benefit from using the QKDLite plugin for strongSwan to make their IPSEC VPNs quantum-safe. For information on how to test the QKDLite plugin for strongSwan, please contact info@pqcee.com
For more details on QKDLite: click here
For plugin installation step-by-step: click here
Author
Clayson Soh
Associate Software Engineer at pQCee with a growing focus on cryptography and quantum computing. Driven by curiosity about emerging technologies and their real-world applications, he's currently exploring the world of cryptography, enjoying solving challenging problems and learning new concepts across the ever-evolving tech landscape.