How to check the post-quantum status of a website?
Websites rely on HTTPS (Hyper-Text Transfer Protocol over Secure Socket Layer) as a means to encrypt information transmitted between the Web browser to Web server. With this data privacy mechanism in place, using the Web to carry out applications such as Internet Banking, eCitizen portals, and even online chatrooms has become a part of our day-to-day lives.
Quantum computers, unfortunately, can break this normalcy. The public key algorithms used in the HTTPS protocol are vulnerable to the "Harvest-now-Decrypt-later" (HNDL) quantum attack, where hackers can collect HTTPS-encrypted communication and use a quantum computer in the near future to decrypt the information. To prevent HNDL attacks, the IETF (Internet Engineering Task Force) has proposed an update for Hybrid key exchange in TLS 1.3 which has been adopted by popular web browsers such as Chrome, Edge, Firefox, and Safari. With this update, websites can become quantum-safe as the information transmitted are encrypted using post-quantum cryptography.
So how do I check if a website is quantum-safe?
Method 1: Check the TLS connection on the browser
When connecting to a website, web browsers will try to find a common encryption method that is mutually supported by both the web browser and web server. If the web server is configured correctly to support the new post-quantum standard, then the HTTPS session will use this method for encryption. You can check this at the web browser based on the following steps:
- Connect to the website you wish to check. You can connect to qkdlite.pqcee.com if you want an example of a website that is using the new post-quantum standard.
- Use the Function F12 shortcut key to get to the "Developer tools" screen, and look for the "Privacy and security" tab.
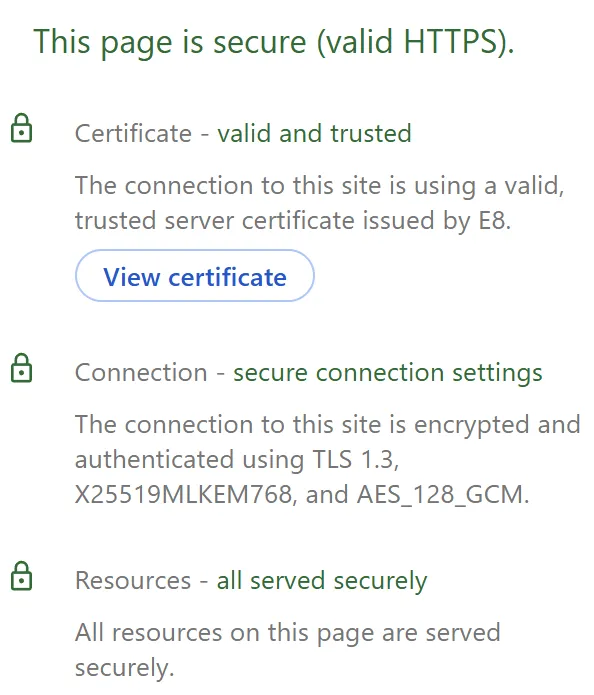
- Under the "Security overview" page, you should be able to see the connection settings used. The figure below shows an example of the Security overview.
- Look out for the X25519MLKEM769 which is the Hybrid Key exchange defined in the post-quantum standard. Using MLKEM768 means that the session key was partly negotiated using the post-quantum algorithm MLKEM and this should make the session key quantum-safe
Method 2: Analyze the network communication using PacketQC
If you want a more comprehensive analysis of the actual communication, you can use pQCee's PacketQC verification tool to check. The steps are as follows:
- You will need to use a packet capture software, e.g. Wireshark, to capture the network packets. If you are using Wireshark, start the packet capture process as described here.
- Connect to the website you wish to check. You can connect to qkdlite.pqcee.com if you want an example of a website that is using the new post-quantum standard.
- Stop the packet capture software. You will now have to save the network packets as a packet capture file, e.g. tcp.pcap.
- Go to PacketQC (https://packetqc.pqcee.com), and upload the tcp.pcap file at the "Choose File" option.
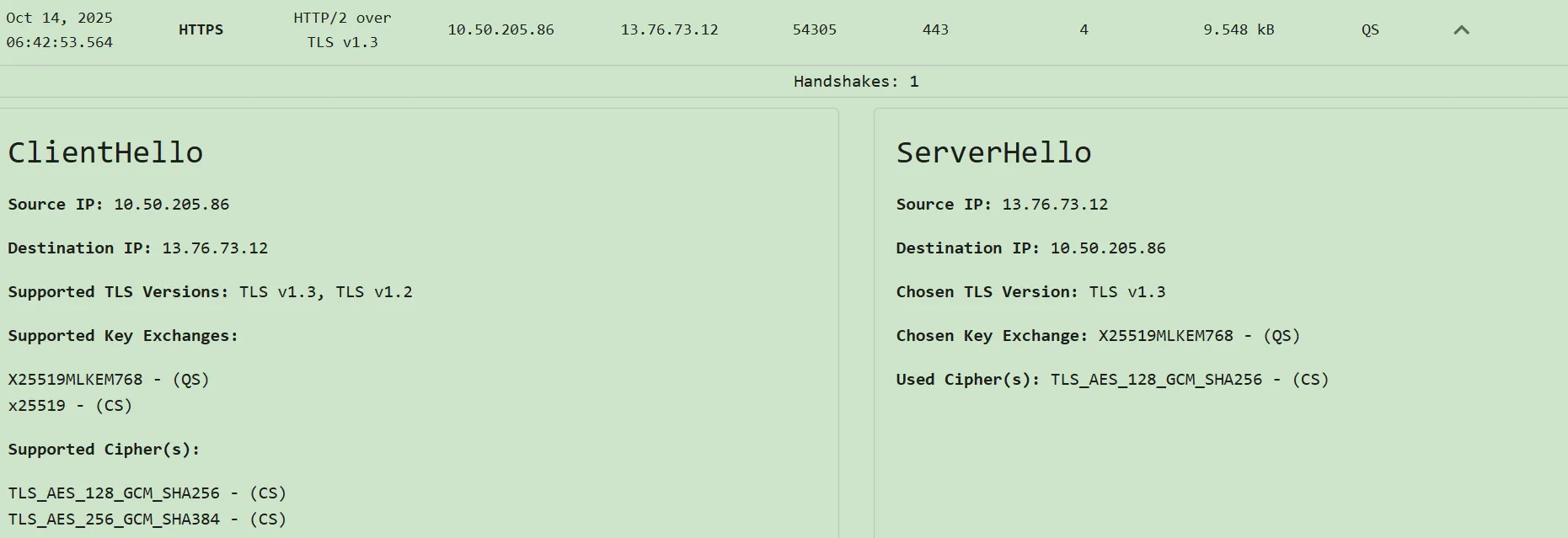
- Click "Generate Security Report", and look at the detailed security report. If you look through your connections, you should find an entry similar to the figure below
- Expanding the entry (image below) will provide you more details on the TLS negotiations where you find that your browser (Client Hello) is capable of both quantum-safe and classical-safe methods, and the eventual chosen key exchange method (Server Hello) is X25519MLKEM768.
What's next
Do note that only key exchange has been standardized to be quantum-safe. Current TLS1.3 authentication is still based on RSA or ECDSA which is classical-safe, but not quantum-safe. It does not yet pose a threat, but we know that websites will need at least 1 more upgrade to fix the authentication before 2030/2031.
If you are looking for help to upgrade your websites to quantum-safe TLS, please visit us at www.pqcee.com or email to info@pqcee.com