5 Surprising Things You May Not Know About p12 Files
Introduction
If you’ve ever worked with certificates, you’ve probably encountered a p12 (or PKCS#12) file. On the surface, it looks simple: just a convenient bundle of your certificate and private key, zipped up with a password. But the truth is, p12 is one of the most misunderstood and underexplored formats in cryptography.
Defined in the PKCS#12 standard (later formalized as RFC 7292), these files were designed as flexible containers for keys, certificates, and related attributes — not just simple bundles. The standard’s flexibility is both its strength and its curse, since most tools only expose a fraction of what the format can actually do.
Digging into its structure feels like opening a black box — or better yet, a matryoshka doll, where each layer reveals something stranger than the last. When I set out to build a p12 myself, every day that I worked on it unveiled a new surprise.
Here are 5 of the most surprising things I learned about p12 files.
1. They’re Not Just Certificates — They’re Containers
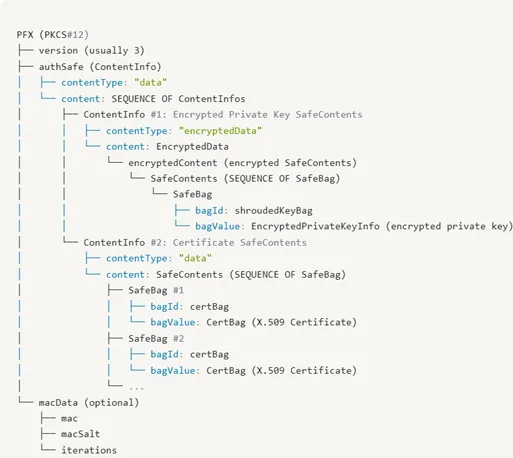
When most people hear “p12 file,” they assume it’s just a certificate bundled up neatly. But that’s only half the story. A p12 is a container — and what it can hold goes far beyond a single certificate. Inside, you might find private keys, certificate chains, friendly names, local identifiers, and even multiple SafeBags nested within one another.
If you peek at a p12 using OpenSSL, you’ll usually see a simplified breakdown: certificate, private key, done. But that output doesn’t do justice to the intricate architecture under the hood. The structure is layered, encoded in ASN.1, and sometimes encrypted in multiple passes, as shown below.
Think of it less like a folder and more like a Russian matryoshka doll, with one encrypted layer hiding another, each piece interlocked with the next.
This container model explains why p12 is both powerful and misunderstood. On one hand, you can ship an entire identity — key plus cert plus chain — in one portable file. On the other, the lack of transparency in its structure means subtle quirks (like mismatched certs and keys, or unexpected encryption choices) often go unnoticed. Once you realize it’s a container, not just a cert, you start treating it less like a static artifact and more like a puzzle box.
2. Understanding ASN.1 Notation Is Crucial
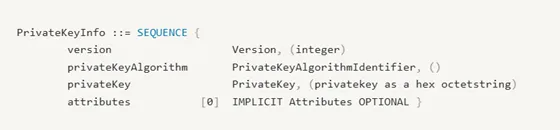
If p12 files feel like puzzle boxes, then ASN.1 is the blueprint. The entire structure of a p12 is described in ASN.1 notation — sequences, sets, choices, and context-specific tags that tell parsers exactly how to read each layer. Without this knowledge, the file is just opaque bytes.
For example, to insert a private key into a p12, it must be structured in the following ASN.1 structure to be even read and processed as a private key:
Why does it matter? Because OpenSSL (and other tools) parse p12 into human-readable form, but sometimes leave out crucial context. For example, the difference between a SafeBag and an EncryptedSafeBag is obvious in ASN.1 but flattened in command-line output. Small changes in ASN.1 — like using long-form lengths or reordering elements — can even make two identical p12s behave differently across systems.
Learning to read ASN.1 notation is like learning to read sheet music. Once you see the patterns, you realize the container isn’t random at all — it’s highly structured, just encoded in a language most developers never learn.
3. The Trust Gap Between the Certificate and the Private Key
Here’s one of the strangest things about p12 files: the container doesn’t care if the certificate and private key actually match. That’s right — you can bundle a private key with a completely unrelated certificate, and most tools will import it without complaint.
This “trust gap” happens because p12 is, at its core, a storage mechanism, not a validation system. It assumes you know what you’re putting inside. So, if you insert a private key generated elsewhere and pair it with a random cert, the container will faithfully hold both. The MAC check will still pass. OpenSSL will still parse it. And when you import it into your OS keychain, chances are it won’t raise a red flag.
The danger, of course, is subtle: just because a p12 loads doesn’t mean it represents a coherent identity. That’s why mismatched p12 files sometimes float around unnoticed — they’re technically valid, just not trustworthy.
This design quirk is a reminder that containers don’t enforce cryptographic binding. The math that ties a certificate to its key isn’t checked at the packaging level. If you want to be sure your p12 is valid, you need to verify it explicitly — don’t assume the container has your back.
4. Private Key Insertion Can Auto-Generate a Public Key
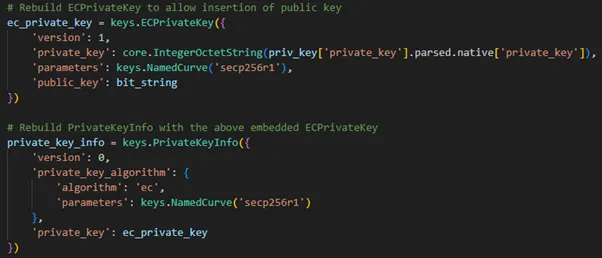
When I first built a p12 programmatically, I hit a weird surprise. Inserting a raw EC private key into the container caused the library to automatically generate a public key on my behalf.
Here’s what happened: ECPrivateKey structures in ASN.1 expect both private and public components. If you provide only the private part, the library assumes you want the full keypair and silently derives the public key for you. Cryptographically, that makes sense — the public key can always be calculated from the private key. But practically, it means the public key inside your p12 may not be the one you expected, unless you explicitly rebuild the key object with your own public component.
This auto-generation step is invisible unless you dig into the raw bytes. To the casual user, the p12 just “works.” But under the hood, the library is doing extra work — and if you’re aiming for deterministic, byte-for-byte reproducible p12s, that hidden magic can trip you up. To solve this problem, I had to rebuild the private key ASN.1 structure using my preferred public key, as shown below:
5. PBKDF2 and the Mystery of ID Values
If you’ve worked with PBKDF2 before, you know the drill: take a password, a salt, an iteration count, and output a derived key. Simple. But in p12 files, PBKDF2 has a twist — it takes an ID value that determines what kind of key it’s generating.
The spec defines three values:
- ID 1 → key encryption
- ID 2 → IV generation
- ID 3 → MAC computation
This means the same password can derive three completely different secrets depending on the ID. For example, the MAC that protects p12 integrity isn’t computed with the same key that encrypts your private key. Instead, it’s derived from the password using ID 3.
Why is this surprising? Because PBKDF2 in most contexts doesn’t use IDs at all. It’s just password → key. But in p12s, the ID is a tiny, invisible gatekeeper. Change the ID, and your password suddenly “stops working.”
This design makes p12 containers more flexible (different components can share the same password safely) but also more confusing. To anyone dissecting a p12, it’s a reminder: the password isn’t the only secret sauce. The ID you feed into PBKDF2 is just as critical.
Conclusion
The p12 format has been around for decades, yet most developers still treat it as a black box. That’s partly because tools like OpenSSL hide the complexity under simple commands, and partly because the spec itself is packed with details most people never dig into.
But once you start peeling back the layers, you realize how much is going on inside: nested containers, invisible key generation, trust gaps, and subtle PBKDF2 behaviours. A p12 isn’t just a file you export once and forget about — each one has a story waiting to be told.
So the next time you see a p12, don’t dismiss it as “just a cert and a key.” There’s a whole world of cryptographic engineering hidden inside, waiting to be unpacked.
Author
Praveenaa U
Praveenaa is an Associate Software Engineer at pQCee. Fascinated by the shift toward quantum-safe cybersecurity, she works on advancing solutions that anticipate tomorrow’s threats — fuelled by her love for representing Singapore in Kabaddi and slowly sipping iced coffee.